Cybersecurity Risk Assessment Explained for Modern Enterprises
- December 23, 2025
- Zunnoor Zafar
Cybersecurity risk assessment serves as the foundational process for identifying and managing cyber threats in modern enterprises.
Attacks like ransomware and phishing dominate headlines, with global data breach costs averaging $4.44 million in 2025. This is down slightly from $4.88 million in 2024 due to improved response times.
To avoid such data breaches and disruptions that could halt operations, these assessments are used. They enable organizations to put proactive defenses in place rather than reactive firefighting. Furthermore, the assessments also align IT, QA and business teams, which is central to enterprise security.
That said, this article will explain what a cybersecurity risk assessment really means for modern enterprises. So, let’s jump in.
Key Takeaways
- Average global breach cost stands at $4.44 million in 2025, climbing to $10.22 million in the US when legal, notification, and revenue losses are included. Cybersecurity risk assessments help enterprises move from reacting after incidents to preventing operational and financial damage in the first place.
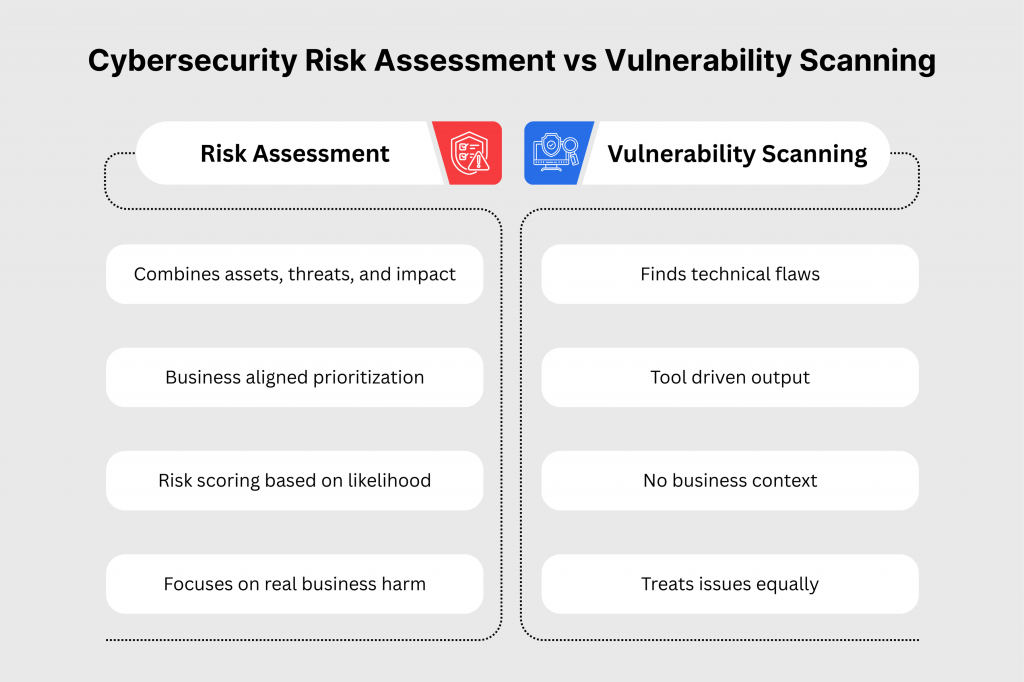
- Modern risk assessments look beyond vulnerability scans by combining assets, threats, likelihood and business impact. This allows teams to focus on risks that can realistically harm the business instead of treating all technical issues equally.
- Threat activity is outpacing enterprise defenses. Ransomware rose 81% year over year, phishing drives 80–95% of breaches, and 32% of critical vulnerabilities remain unpatched for over 180 days. This makes structured risk prioritization essential.
- Cloud and third-party ecosystems have become major risk drivers. Cloud misconfigurations account for 80% of security exposures, while supply chain attacks average 28 per month in 2025. This expands the attack surface beyond internal systems.
- Risk assessments deliver real value only when embedded into QA and daily operations. Enterprises that tie risk scoring to testing reduce production vulnerabilities, especially as data breaches have increased 72% in recent years.
What Is a Cybersecurity Risk Assessment?
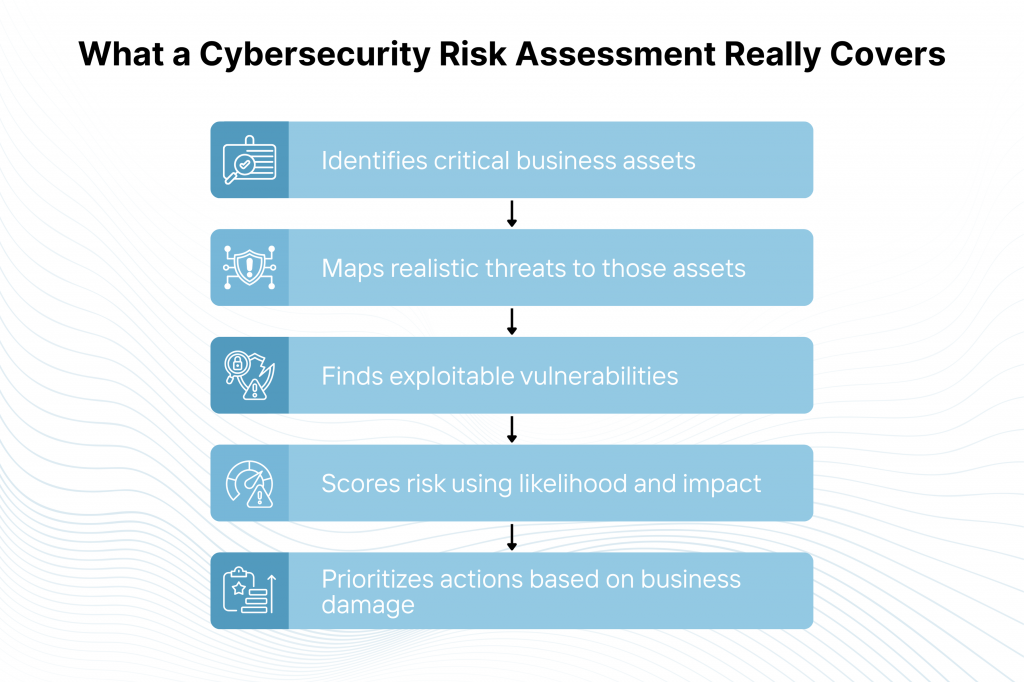
A cybersecurity risk assessment is a structured, enterprise-wide process. It systematically identifies critical assets, as well as potential threats, existing vulnerabilities and their associated business impacts. This is done to quantify, prioritize and mitigate risks effectively.
This assessment is unlike narrow vulnerability scans, which solely pinpoint technical flaws like unpatched software. It incorporates threat likelihood, along with impact severity and unique organizational context. This context can be regulatory environments or supply chain dependencies. All this is done to deliver prioritized, actionable mitigation plans rooted in real-world enterprise operations.
For modern enterprises, this evaluation spans diverse landscapes, including cloud infrastructures, IoT devices, SaaS applications and third-party vendors. It is ensured that there is comprehensive coverage of the expanded attack surface.
Key distinguishing features include:
- Holistic Scope: Combines assets (e.g., customer data, ERP systems), threats (e.g., ransomware), and vulnerabilities (e.g., weak access controls) into a unified risk profile.
- Quantitative Scoring: Uses models like likelihood × impact matrices (e.g., 5×5 grids) to assign numerical risk levels. This helps you make data-driven decisions over subjective judgments.
- Business Alignment: Factors in enterprise-specific consequences, such as downtime costs or compliance fines, rather than isolated technical metrics.
- Iterative Nature: Produces living outputs like risk registers that feed into QA test planning, incident response and continuous improvement cycles.
Security risks do not wait. Neither should you.
Contact Kualitatem today to start a structured risk assessment.
Why Cybersecurity Risk Assessments Matter for Modern Enterprises
Remember the $4.44 million figure we talked about earlier? It goes up to $10.22 million in the United States when you factor in legal fees, customer notifications and lost business opportunities.
This underscores the urgent financial imperative for proactive risk assessments. Beyond direct economics, these assessments also avert crippling operational downtime. All while shielding against reputational damage from high-profile incidents, such as ransomware attacks that can paralyze production lines or supply chains, which erode customer trust and market value.
They also ensure compliance with stringent mandates like GDPR and HIPAA, dodging multimillion-euro fines. But the best news for you is that these assessments can be integrated directly into QA and assurance workflows to prioritize testing on high-risk areas. Doing so curbs defect escapes amid a 72% surge in data breaches over recent years.
Apart from this, the stakes also extend across multiple dimensions. Cybersecurity risk assessments allow organizations to:
- Mitigates losses from downtime (average 21 days for ransomware recovery) and recovery efforts, with U.S. breaches costing 2.3x the global average due to regulatory scrutiny.
- Prevent disruptions like halted manufacturing or e-commerce outages, where 60% of enterprises report revenue impacts exceeding 10% from incidents.
- Counter brand erosion, as 87% of consumers avoid companies post-breach, amplifying long-term revenue hits.
- Generate audit trails for GDPR (fines over €284 million total) and HIPAA ($129.7 million in penalties), proving due diligence in regulated sectors.
- Feed risk data into test strategies, reducing production vulnerabilities by focusing on threats like unpatched code, leading to better software assurance.
Prevention costs less than recovery. Always.
Get a quote from Kualitatem today and plan risk mitigation before it turns real.
Core Components of a Cybersecurity Risk Assessment
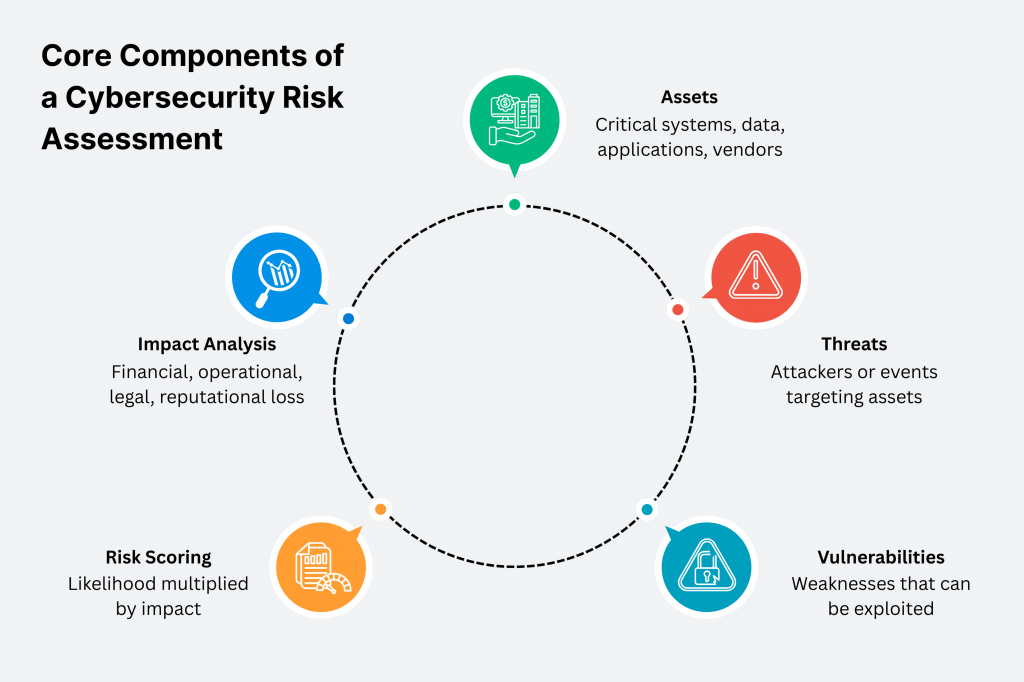
All the core components of a cybersecurity risk assessment form an interconnected framework. One that systematically breaks down the enterprise attack surface into manageable elements. This enables you to come up with precise risk quantification and mitigation.
With that said, the main components are:
1. Assets
These represent the foundational targets of potential attacks. Assets include tangible items like customer databases, servers and IoT devices. As well as intangible ones, such as intellectual property, SaaS applications and third-party integrations.
Enterprises must inventory and classify the assets by criticality (e.g., high-value crown jewels like payment systems), as they define the scope and potential blast radius of any compromise.
2. Threats
Threats are the external or internal actors or events capable of exploiting weaknesses. These can be phishing campaigns (responsible for 54% of ransomware entry points), ransomware deployments, state-sponsored espionage or insider misuse.
You must understand threat actors’ tactics, techniques, and procedures (TTPs) via sources like MITRE ATT&CK. This will help predict likely attack vectors tailored to your enterprise’s industry and profile.
3. Vulnerabilities
Vulnerabilities are defined as specific weaknesses in assets that threats can exploit. They can range from unpatched software flaws (e.g., Log4j vulnerabilities) and misconfigured cloud storage to weak access controls or outdated encryption protocols.
These are uncovered through scans and audits, with prioritization based on exploitability rather than just existence.
4. Risk Scoring
It is a quantitative method that multiplies threat likelihood (e.g., on a 1-5 scale based on historical data) by vulnerability impact to generate a risk level (e.g., low/medium/high).
Models like 5×5 matrices or CVSS scores provide objectivity, allowing QA teams to focus testing on top-scored items.
5. Impact Analysis
Impact analysis basically means to evaluate the downstream consequences of exploitation. The analysis encompasses financial losses (e.g., ransom payments or recovery costs), operational disruptions (e.g., halted production), legal penalties (e.g., GDPR fines), and reputational damage (e.g., customer churn).
This business-contextual layer ensures security aligns with enterprise priorities beyond technical fixes.
Risk assessment works best when backed by real execution. Take a look at the testing and security services Kualitatem offers.
Step-by-Step Cybersecurity Risk Assessment Process
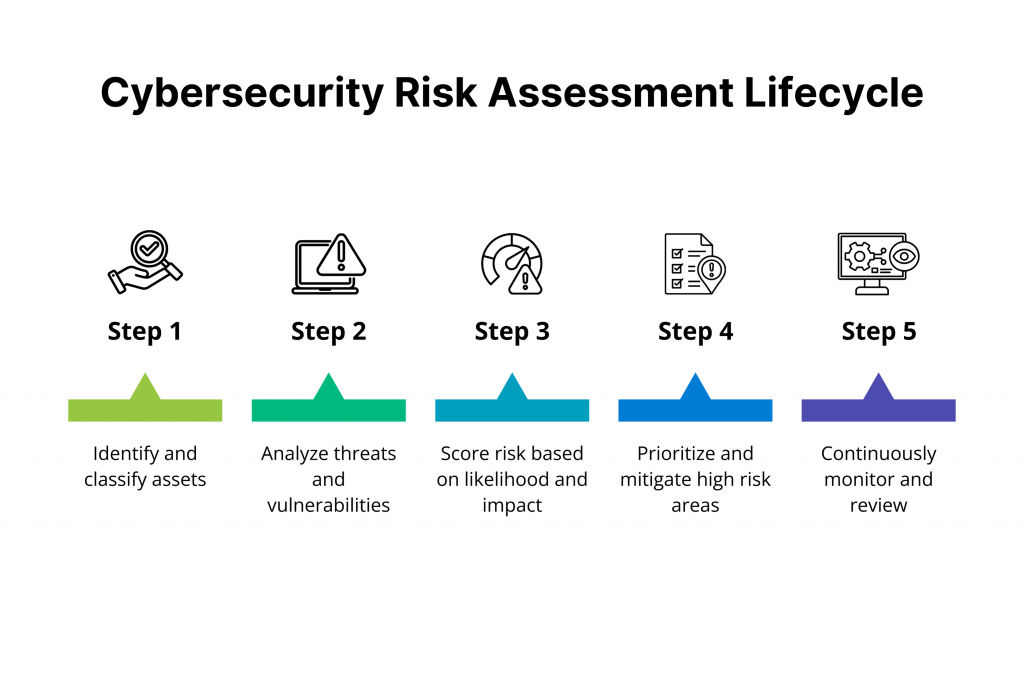
The process of cybersecurity risk assessment unfolds across five sequential yet iterative steps, which are as follows.
Step 1: Asset Identification
Begin by creating a comprehensive inventory of all enterprise assets. They would include hardware (servers, endpoints), software (applications, SaaS tools), data (customer records, IP), and people/processes that form the attack surface.
Then classify the assets by criticality, such as tier-1 crown jewels like payment gateways. This can be done by using tools like CMDBs or automated discovery scanners to uncover shadow IT and third-party dependencies.
Do note that this step has to be carried out with extreme diligence, as it is the foundation that will ensure no blind spots. Done right, the QA teams will be directly informed of which components demand rigorous testing.
Step 2: Threat and Vulnerability Analysis
Now it’s time to identify potential threats (e.g., phishing actors, ransomware groups) and vulnerabilities (e.g., unpatched CVEs, misconfigurations) through a multi-method approach.
This approach includes automated scans (Nessus/Qualys), employee interviews, log reviews and threat intelligence feeds like MITRE ATT&CK.
You also have to map threats to assets to assess exploitability, based on real-world TTPs, to build a threat model tailored to your industry. Such as supply chain risks for manufacturing.
This phase uncovers interconnections, like a vulnerable API exposing core databases.
Step 3: Risk Analysis and Scoring
Next up, quantitatively evaluate identified risks by analyzing likelihood (historical attack frequency) against impact (business consequences).
This can be done using standardized models like 5×5 matrices or CVSS v4.0 scores to assign numerical values. For example, e.g., a high-likelihood phishing vector on a critical asset scores 25/25 (critical).
Also, incorporate qualitative inputs from stakeholders to refine scores, prioritizing “heat map” visualization for executive review and QA test case generation on top risks.
Step 4: Prioritization and Mitigation Planning
Rank risks by score, focusing resources on high/medium threats via cost-benefit analysis, e.g., patching vs. segmentation for a CVSS 9.8 flaw.
You have to develop tailored mitigation strategies, such as zero-trust access controls, employee training or vendor audits, with assigned owners, timelines, and budgets.
Another thing you can do is integrate into enterprise roadmaps to link mitigations to QA cycles for vulnerability-informed automation scripts. This will ensure swift implementation without overwhelming dev teams.
Step 5: Continuous Monitoring and Review
Lastly, when everything is done, you have to establish ongoing surveillance through SIEM dashboards.
Set up automated alerts and quarterly reassessments that are triggered by events like patches, mergers or incidents.
Also track mitigation effectiveness with KPIs (e.g., mean time to remediate), update the risk register dynamically, and conduct post-mortem analyses.
This living cycle feeds back into QA for adaptive testing and gives you a resilient posture amid evolving threats like AI-driven attacks.
Theory is easy. Execution proves value.
Read Kualitatem case studies to see how enterprises reduced real risk.
Common Enterprise Threats and Vulnerabilities
Enterprises confront a diverse array of cyber threats and vulnerabilities. Ones that exploit modern digital infrastructures. Phishing and ransomware lead as primary vectors responsible for the majority of breaches.
These risks amplify in scale due to hybrid cloud environments, remote workforces, and interconnected supply chains. They also demand vigilant identification within risk assessments to safeguard QA pipelines and operational integrity.
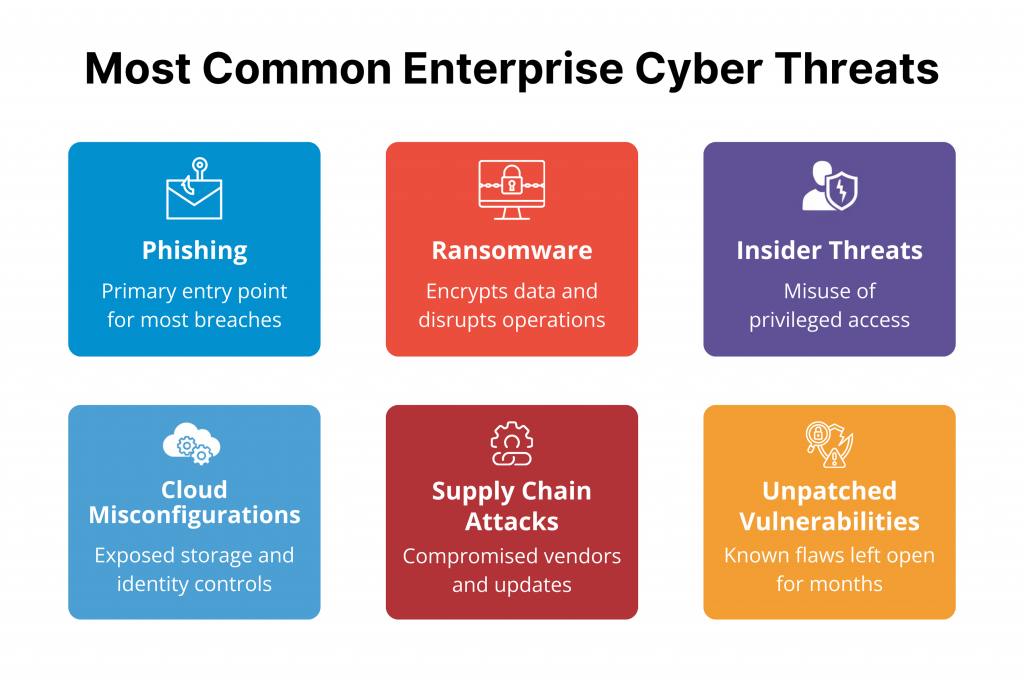
Key threats and vulnerabilities include:
- Phishing Attacks:
The most prevalent entry point, driving most of the ransomware infections and 80-95% of all breaches by tricking users into revealing credentials, clicking malicious links or downloading malware-laden attachments.
Spear-phishing targets executives for wire fraud, while business email compromise (BEC) siphons millions annually. The need for simulated training integrated into QA user acceptance testing has seen an increase due to phishing attacks.
- Ransomware:
Ransomware experienced an 81% year-over-year surge from 2023 to 2024. When an attack happens, critical data is encrypted, and payment is usually demanded. $1.54 million per ransomware incident is the average, often via initial phishing or exploited vulnerabilities.
Furthermore, double-extortion tactics now exfiltrate data pre-encryption for added leverage, crippling sectors like healthcare and manufacturing with prolonged downtime.
- Insider Threats:
Responsible for 60% of data breaches, these arise from accidental misconfigurations or malicious actions by employees with privileged access. Insider threats have risen by 47% in incidents since 2018.
They cause outsized damage through data exfiltration, underscoring behavioral analytics in QA user access testing.
- Cloud Misconfigurations:
These drive 80% of security exposures overall and 23% of cloud incidents, with 56% impacting critical cloud assets like unsecured S3 buckets or IAM roles.
Cloud misconfigurations lead to lateral movement from on-premises to cloud. Rapid scaling amplifies these in hybrid setups.
- Supply Chain Compromises:
Such threats averaged over 28 attacks per month since April 2025. Almost double the prior levels. With IT (nearly 120 incidents) and finance (over 80) hardest hit by groups like Qilin and Akira via tainted software updates.
- Unpatched Vulnerabilities:
32% of critical flaws remain exposed over 180 days, fueling a 54% surge in attacks on known CVEs in 2024, as daily disclosures hit 115 on average.
Legacy systems perpetuate this risk, demanding patch prioritization in QA cycles.
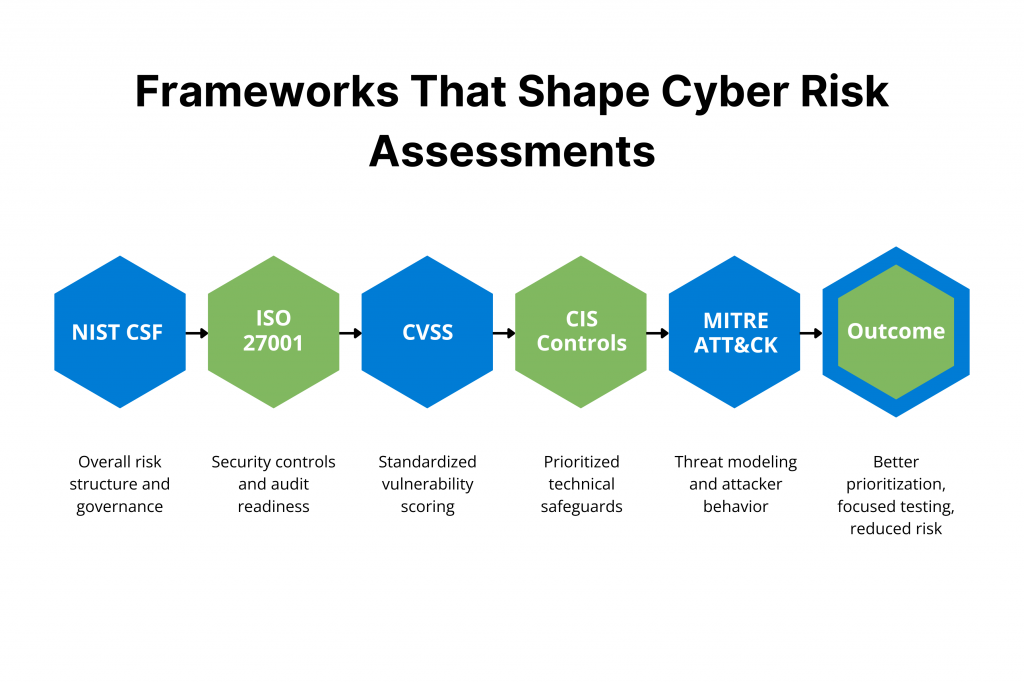
Frameworks and Standards Used in Cyber Risk Assessments
Frameworks and standards provide structured methodologies for conducting cybersecurity risk assessments. They offer enterprises proven blueprints to identify, manage, and mitigate risks consistently across operations.
And not just that, these also bridge technical implementation with business strategy. QA teams easily align testing with standardized security controls and compliance needs in dynamic environments.
That said, leading frameworks and standards are listed below.
NIST Cybersecurity Framework (CSF)
Widely adopted by 83% of companies per 2025 CISO benchmarks, NIST CSF organizes risk assessments into five core functions, which are:
- Identify
- Protect
- Detect
- Respond
- Recover
These functions provide a flexible, outcome-based structure for all organizational sizes.
The framework’s CSF 2.0 updates emphasize governance and supply chain risks. With healthcare at 68% adoption, finance at 81%, and SMEs reaching 42%. This makes it ideal for hybridizing with QA pipelines to prioritize vulnerability testing.
ISO 27001
This is an international standard for information security management systems (ISMS). It specifies 93 controls across 14 domains (updated from 114 in prior versions) to establish, maintain and continually improve security.
ISO 27001 excels in audit certification, requiring risk treatment plans that integrate with enterprise QA for control validation through automated and manual tests.
CVSS (Common Vulnerability Scoring System)
A standardized metric from FIRST.org scoring vulnerabilities 0-10 based on exploitability, impact, and complexity factors (e.g., CVSS v4.0 adds threat metrics).
CVSS is used universally in assessments to prioritize patches. It feeds QA tools like scanners for risk-informed test case generation on high-CVSS flaws.
CIS Controls (Center for Internet Security)
CIS Controls include 18 prioritized safeguards (Implementation Groups 1-3) derived from real-world threats, focusing on asset inventory, access control, and continuous vulnerability management.
Enterprises hybridize with NIST for practical roadmaps, especially in manufacturing (57% adoption) and SMEs seeking quick wins without full ISO overhead.
Other Models
Some other notable frameworks and standards for cyber risk assessments are:
- COBIT for governance integration
- MITRE ATT&CK for threat modeling
- Industry-specific, like PCI-DSS (payment security) or HIPAA (health data), are often layered atop NIST for tailored enterprise assessments.
Frameworks guide direction. Experience drives outcomes.
Know more about Kualitatem’s cybersecurity and QA consulting.
Tools and Platforms for Cybersecurity Risk Assessment
Tools and platforms are used to automate cybersecurity risk assessments. Enterprises use them to shift from manual spreadsheets to scalable, data-driven processes that integrate with QA and DevSecOps workflows.
The following solutions handle asset discovery, vulnerability scanning, threat analysis, risk scoring, and continuous monitoring. You get real-time dashboards and automated reporting for executive visibility and compliance audits.
1. Vulnerability Scanners
Qualys and Tenable Nessus (formerly Nessus) perform automated asset discovery, flaw detection and prioritization using CVSS scores. They are able to scan thousands of endpoints, cloud instances and containers daily.
These tools generate QA-actionable reports for you. You can easily prioritize tests on CVSS 9+ flaws and reduce manual pentesting significantly in large enterprises.
2. SIEM and Threat Detection
Splunk, Elastic SIEM and Microsoft Sentinel aggregate logs for real-time threat hunting, as well as anomaly detection and behavioral analytics.
These tools correlate events across hybrid environments. Integration with QA pipelines flags risky code deployments, such as unpatched dependencies, supporting shift-left security in CI/CD.
3. GRC Platforms
RSA Archer, ServiceNow Security Operations and OneTrust centralize risk registers, along with policy management and workflow automation.
You get customizable dashboards for tracking mitigation progress and generating audit trails. These tools also bridge security and QA by linking risks to test cases, automating remediation tickets in Jira or Azure DevOps.
4. Cloud-Native Tools
AWS Security Hub, Azure Defender, and Google Chronicle analyze cloud-specific risks like IAM misconfigurations or S3 exposures.
They provide native integrations for auto-remediation and feed risk data into QA for cloud workload testing, essential as 80% of breaches involve cloud assets.
5. Integrated Risk Platforms
Bitsight and UpGuard offer third-party risk monitoring and continuous exposure management, scoring vendor security postures alongside internal assets.
For QA, these tools enable supply chain testing, ensuring dependencies meet security baselines before production.
Best Practices for Effective Cybersecurity Risk Assessments
Effective cybersecurity risk assessments demand disciplined execution beyond one-off exercises.
Your goal should be to transform the assessments into living processes that align security with enterprise goals, QA workflows and compliance. To do this, follow the best practices mentioned below.
1. Establish a Regular Assessment Cadence
Adopt a quarterly cadence for high-risk enterprises (e.g., finance, healthcare) and annual reviews for stable ones. Also enable ad-hoc triggers like major deployments, mergers, or incidents.
This frequency aligns with NIST recommendations, preventing risk staleness amid evolving threats, while scaling effort via automated tools to avoid overwhelming QA cycles.
2. Secure Executive Buy-In and Sponsorship
Gain C-level commitment early by framing assessments in business terms, e.g., breach costs vs. prevention ROI. Additionally, assign a senior champion to enforce participation and resource allocation.
Community discussions highlight this as the top blocker, turning checkbox exercises into strategic imperatives with budget for tools and training.
3. Foster Cross-Team Collaboration
Involve security, IT, QA, development and business units from kickoff through remediation. To achieve this, use shared platforms like Jira for risk tickets and workshops for input.
This breaks silos and enriches threat models with diverse perspectives (e.g., QA flags code vulns). Mitigations also stick across the organization.
4. Automate Routine Tasks and Scans
Leverage tools like Qualys for vuln scanning and Splunk for log analysis to minimize manual spreadsheet work. This will free analysts for high-value scoring and planning.
Automation cuts assessment time by half and integrates with CI/CD for real-time QA feedback. It also scales to enterprise volumes without proportional headcount.
5. Maintain Living Risk Registers and Documentation
Document findings in dynamic registers (e.g., ServiceNow GRC) rather than static PDFs. Track ownership, status and residual risks with version control.
Also, don’t forget to include post-incident lessons and KPIs like remediation velocity. Always feed updated data back into QA test suites for continuous assurance.
6. Prioritize Actionable, High-Impact Risks
Focus on threats with realistic compromise potential using quantitative scoring. Avoid analysis paralysis on low-likelihood scenarios.
Furthermore, tie prioritization to business impact. The users in Reddit QA communities often advise to “prioritize what can actually hurt you,” and we can’t agree more.
Challenges in Conducting Assessments
Cybersecurity risk assessments often falter. Not from technical complexity but from organizational and procedural hurdles.
Drawing from real-world frustrations shared by users, let’s discuss some of the challenges faced by QA peeps while conducting cybersecurity risk assessments.
1. Manual Processes and Spreadsheets Dominate
One user on Reddit lamented, “Most teams are still stuck in manual risk work (evidence, registers, spreadsheets),” explaining that people default to Excel because it is “fast and familiar.”
However, spreadsheets often lead to errors, delays and outdated data that hampers QA integration.
2. Lack of Leadership Buy-In and Team Alignment
Users frequently complain, “The biggest blocker is not the framework, it is people and alignment,” with GRC pros noting they end up “chasing teams for inputs and getting delayed or ignored because delivery teams are swamped with ‘more urgent’ work.”
This turns assessments into mere checkbox exercises and not something that can genuinely help you.
3. Treating Assessments as One-Off Events
As another Redditor pointed out, “Many companies treat risk assessment as a one-off event, not a living cycle.”
Due to this, reports get filed away even though the risks change constantly, leaving QA disconnected from evolving priorities.
4. Vendor and Third-Party Risk Reviews Are Painful
Users in online communities criticize vendor security reviews as “tedious and coming too late,” often forced to “rubber-stamp or fight” after business decisions are made.
This timing mismatch leads to rushed assessments, overlooked supply chain risks and friction that delays QA validation of third-party integrations.
Closing Thoughts
Cybersecurity risk assessment is not just a security task or a compliance formality. It is a business habit. Modern enterprises change fast, and attackers move even faster. If risk reviews sit in a folder and never get updated, they lose all value.
The advice is that organizations treat risk assessment as something ongoing. It should live inside QA, DevOps, and daily decision-making. Teams should use it to decide what to test first, where to invest and which risks can wait. This keeps security practical, not theoretical.
You do not need to predict every attack. You need clarity on what could realistically hurt your business and the discipline to act early.
Kualitatem provides cybersecurity advisory and security services. Engage our Cybersecurity Advisory to assess, prioritize and reduce risk.
Frequently Asked Questions (FAQs)
Q) What is a cybersecurity risk assessment?
A systematic process that identifies enterprise assets, threats, vulnerabilities and impacts. Risks are categorized by likelihood and severity to prioritize mitigations like patching or training.
Q) What are the key steps in a cybersecurity risk assessment?
The key steps are: Asset identification, threat/vulnerability analysis, risk scoring, mitigation planning, and continuous monitoring. These are often quarterly for critical areas.
Q) How often should cybersecurity risk assessments be done?
Quarterly for high-risk operations and once annually minimum. Assessments can also be carried out post-events, like deployments, and in a risk-based manner to focus on critical assets efficiently.
Q) What frameworks support cybersecurity risk assessments?
NIST CSF, ISO 27001 for controls, and CVSS for scoring. These can be hybridized for enterprise needs.
Q) What are common cybersecurity threats enterprises should assess?
Phishing attacks, ransomware, insider threats, cloud misconfigurations, supply chain compromises, and unpatched vulnerabilities.