Security Testing in the Software Development Lifecycle
- December 18, 2025
- Zunnoor Zafar
Security Testing in SDLC integrates vulnerability detection across all development phases. It enables a secure development environment that prevents breaches and other vulnerabilities. This secure approach reduces risks by up to 60% through early fixes.
However, modern threats like ransomware and supply chain attacks demand security shift-left testing in SDLC. This means that you have to integrate checks into Agile and CI/CD pipelines for faster, safer releases.
That said, today we’ll talk all about security testing in the software development lifecycle. So, let’s start.
What is Security Testing in SDLC?
Finding weaknesses, hazards and risks in software applications and infrastructure is done through security testing.
It can be done manually, or you can automate the processes, from code scans to simulated attacks. This ensures that the application resists exploits like SQL injection.
The primary objective of it is to ensure that the software and the associated data are protected against unauthorized access, misuse and theft. A secure SDLC follows frameworks like NIST SSDF or OWASP and prioritizes doing things the “shift-left” way in SDLC to catch issues pre-production. Due to this, fixing costs are slashed 100x versus post-deployment.
A range of techniques and tools can be used to detect and mitigate security risks in software applications. More on this below.
Looking for expert guidance on security testing? Reach out to Kualitatem for tailored solutions.
Why is Security Testing Important in the SDLC and Why it Matters Today
As mentioned earlier, security testing in SDLC plays a pivotal role by embedding proactive vulnerability detection from the outset. It changes security from a reactive afterthought into a core driver of resilient software.
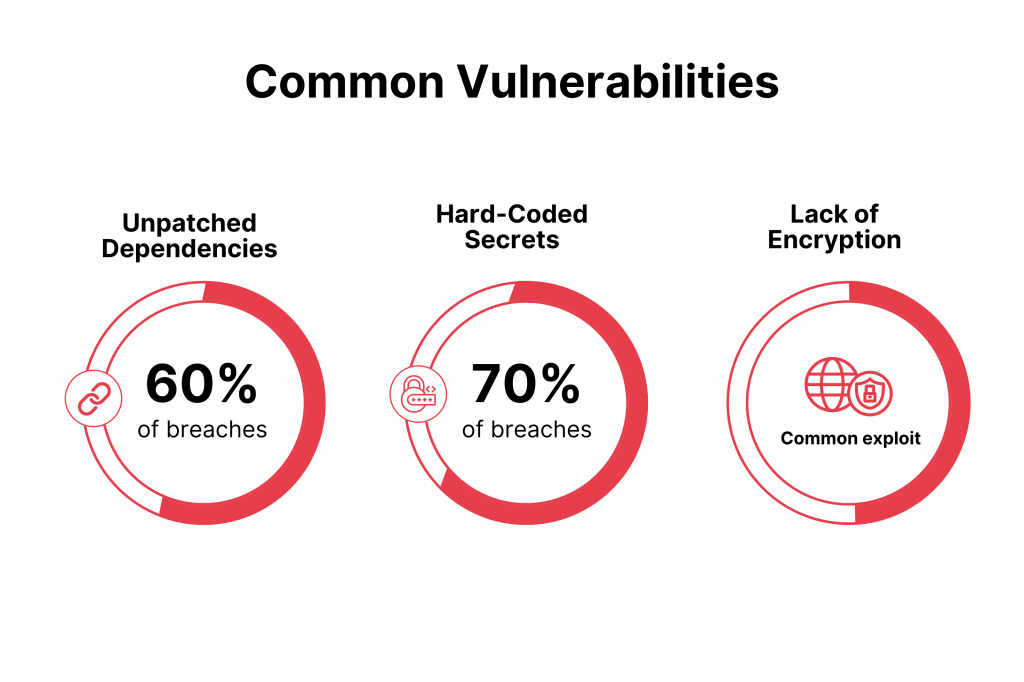
This results in the prevention of costly breaches, which averaged $4.88 million globally in 2024, often stemming from overlooked flaws like unpatched dependencies that expose systems to exploits.
Additionally, ransomware threats underscore the urgency, with incidents surging in 2025 and driving recovery costs into the millions due to extended downtime. Many trace back to SDLC gaps in early validation.
Then you also have the regulations. They intensify the stakes even further. To put this into perspective, GDPR alone issued €1.2 billion in fines in 2024, with potential penalties reaching 4% of global annual revenue for non-compliance. Hence, organizations must prioritize security testing best practices.
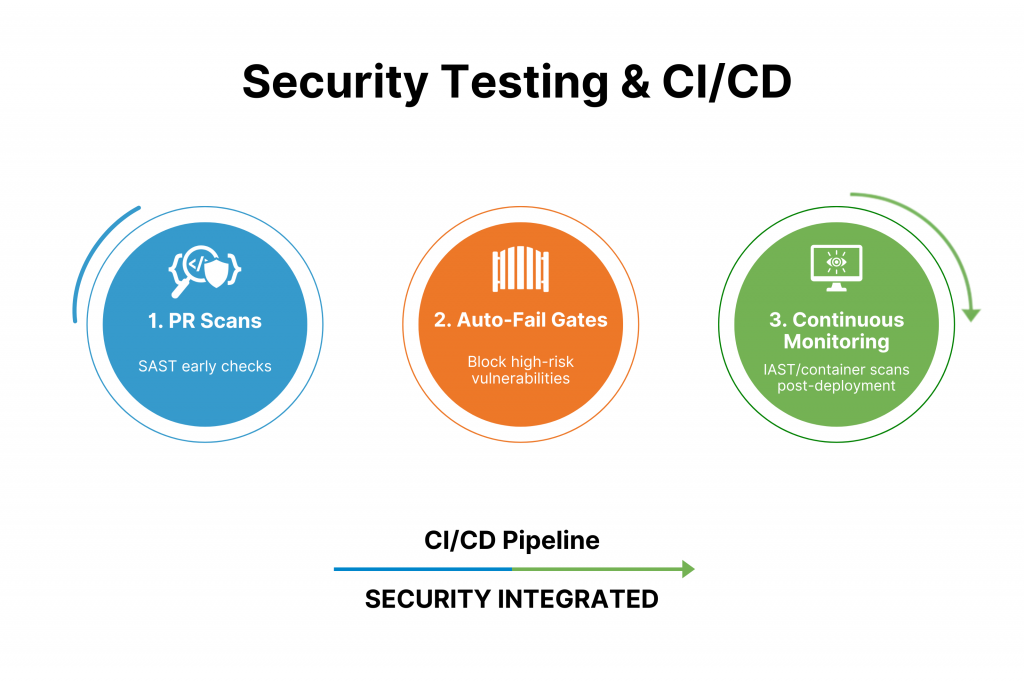
Development teams frequently grapple with pain points like late-stage discoveries that derail Agile sprints, inflate costs and erode trust. Shift-left security testing in SDLC, along with Develops counter this by integrating automated scans into CI/CD pipelines early.
Types of Security Testing and When to Use Them
The security testing lifecycle balances manual vs automated security testing to deliver comprehensive coverage, addressing both code-level flaws and runtime behaviors across SDLC phases.
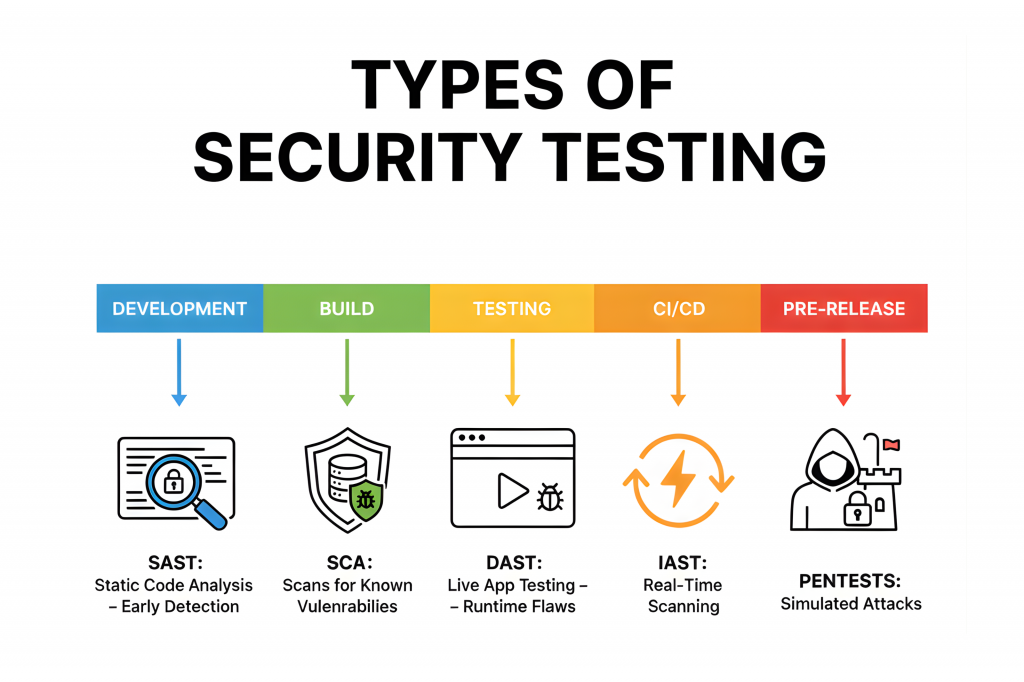
1. SAST (Static Application Security Testing)
SAST scans source code without execution, detecting issues like buffer overflows, SQL injection risks or insecure deserialization early in development.
It is ideal for shift-left security testing in SDLC, as it empowers developers via IDE plugins, catching 85% of vulnerabilities before builds.
Tools like SonarQube and Checkmarx integrate seamlessly into Git workflows, enforcing secure coding standards proactively.
2. DAST (Dynamic Application Security Testing)
DAST probes live, running applications from an external perspective, uncovering runtime flaws such as XSS, CSRF, or broken authentication.
Best suited for the testing phase, it simulates black-box attacks like real hackers, validating defenses in staging environments. OWASP ZAP and Burp Suite excel here, providing realistic exploit simulations without source access.
3. IAST (Interactive Application Security Testing)
IAST combines SAST and DAST in real-time during app execution, offering precise detection of logic errors, as well as API vulnerabilities and data leaks with minimal false positives.
Deploy it in CI/CD pipelines for continuous feedback, bridging development and production realism. Contrast Security and Synopsys lead this space, instrumenting apps for hybrid insights.
4. SCA (Software Composition Analysis)
SCA audits open-source dependencies and third-party libraries for known CVEs, license risks, and outdated components. This is critical since 60% of breaches originate from vulnerable libs.
Run it at the build stage to block risky pulls automatically. Snyk and Black Duck provide policy-as-code enforcement, tying directly into DevSecOps security testing.
5. Manual Penetration Testing
Manual pentests leverage human expertise to simulate sophisticated attacks. These attacks uncover business logic flaws, chaining exploits or social engineering vectors that tools miss.
You can schedule design reviews and pre-release gates that complement automation for nuanced threats.
Furthermore, ethical hackers using Metasploit or custom scripts deliver detailed reports with remediation roadmaps.
| Type | Description | Best Phase | Tools/Example | Coverage Strength |
| SAST | Analyzes source code for issues like buffer overflows | Development (shift-left) | SonarQube, Checkmarx | 85% early detection |
| DAST | Probes running apps for runtime flaws like XSS | Testing | OWASP ZAP, Burp Suite | Black-box realism |
| IAST | Real-time hybrid scanning for logic errors | CI/CD | Contrast Security | Low false positives |
| SCA | Scans dependencies for known CVEs | Build | Snyk | 60% of breaches from libs |
| Manual Pentest | Simulates human-led attacks | Design/Pre-Release | Ethical hackers | Nuanced threats |
Explore Kualitatem’s trusted clients and see how we’ve secured leading brands across industries like finance, healthcare, and tech.
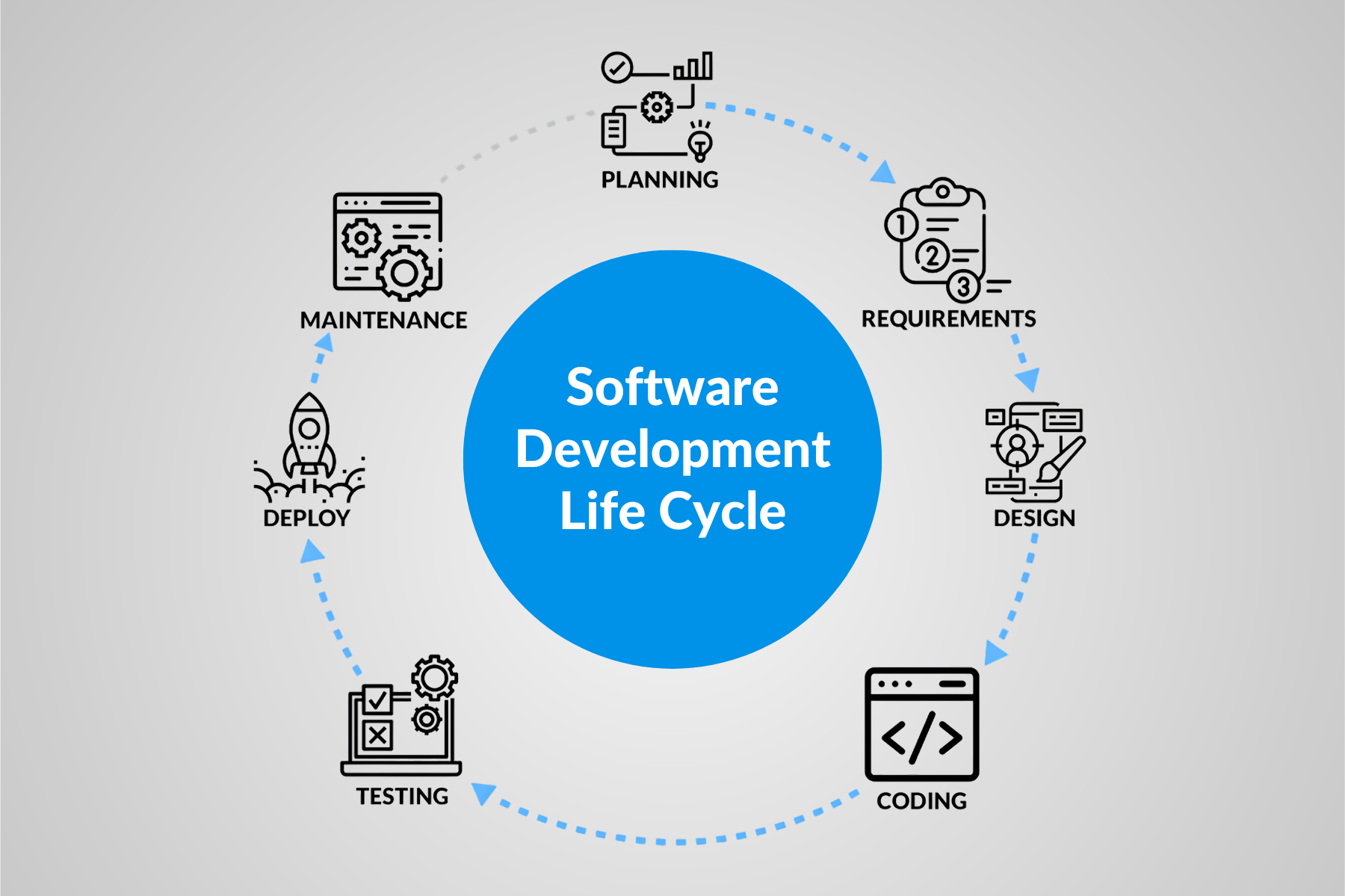
Integrating Security Across SDLC Phases
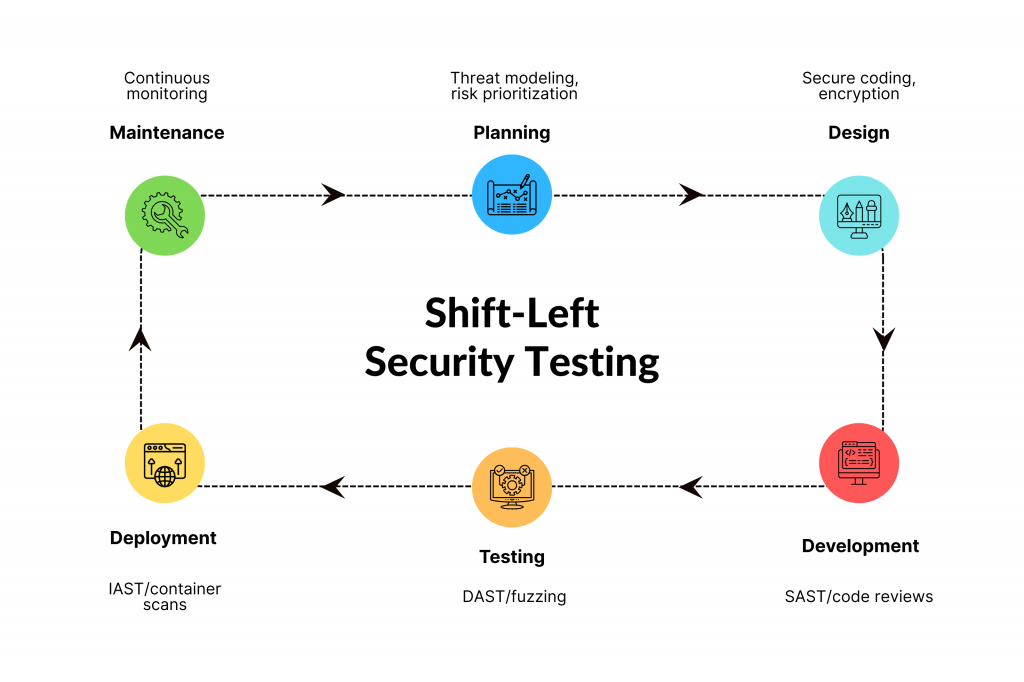
Security shift-left in SDLC weaves testing into every phase, enabling continuous security testing and CI/CD gates that automate enforcement without slowing delivery.
- Planning: Conduct threat modeling using STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) to identify risks early. Also, define clear security requirements and compliance needs like GDPR. Doing so aligns teams upfront to address potential flaws proactively.
- Design: Integrate robust controls such as OAuth 2.0 for authentication, AES-256 encryption for data at rest/transit, and a zero-trust architecture to verify every access request. This ensures security is baked into blueprints rather than bolted on later.
- Development: Run SAST scans and peer code reviews directly in IDEs like VS Code. Another thing you can do is automatically block hard-coded secrets or API keys through linters and pre-commit hooks, fostering secure coding habits from the start.
- Testing: Execute DAST for runtime probes. Fuzzing to stress inputs with malformed data. Full penetration tests in isolated QA environments to validate end-to-end defenses against real-world attack patterns.
- Deployment: Perform IAST for interactive analysis, container/image vulnerability scans with tools like Trivy, and blue-green deployments with automated fail-gates that block releases on critical issues.
- Maintenance: Implement SIEM tools like Splunk for real-time monitoring and anomaly detection. You can also schedule quarterly reassessments and patch management to counter new vectors introduced by updates.
In CI/CD pipelines (e.g., Jenkins, GitHub Actions), configure gates to auto-fail builds on high-CVSS vulnerabilities. All while generating PR comments for low-risk fixes to ensure smooth DevSecOps security testing.
See how enterprises reduced risk with real case studies from Kualitatem – Get inspired by proven security wins.
Tools and Automation for SDLC Security
SDLC security tools form the backbone of DevSecOps security testing. They automate scans to integrate into CI/CD pipelines and reduce manual overhead for QA teams.
Getting Started with Integrations
Start with lightweight integrations: Embed SAST scanners in pull requests (PRs) via GitHub Actions or GitLab CI. These provide instant feedback to developers without disrupting workflows.
They also empower Agile teams to fix flaws collaboratively, aligning with security testing best practices.
Network and Penetration Testing Tools
Classics like Burp Suite and Nessus excel in intercepting traffic and vulnerability scanning. On the other hand, Nmap maps open ports and services, and Wireshark analyzes packets for anomalies. These are essential for real-world reconnaissance.
Additionally, Metasploit advances this with exploit frameworks for testing defenses in controlled environments.
Modern SCA and IAST Solutions
Snyk detects vulnerable open-source dependencies early in builds, preventing risky libraries.
OWASP ZAP delivers free DAST for web apps with custom scripting, and Contrast Security offers runtime IAST for precise, low-false-positive alerts.
Enterprise Security Services
Kualitatem complements tools with security testing services, including penetration testing, vulnerability assessments and managed audits.
Our services unify QA and security for compliance and risk management. Trusted by global enterprises like FedEx and United Airlines.
Ready to secure your SDLC? Get a free security assessment quote today.
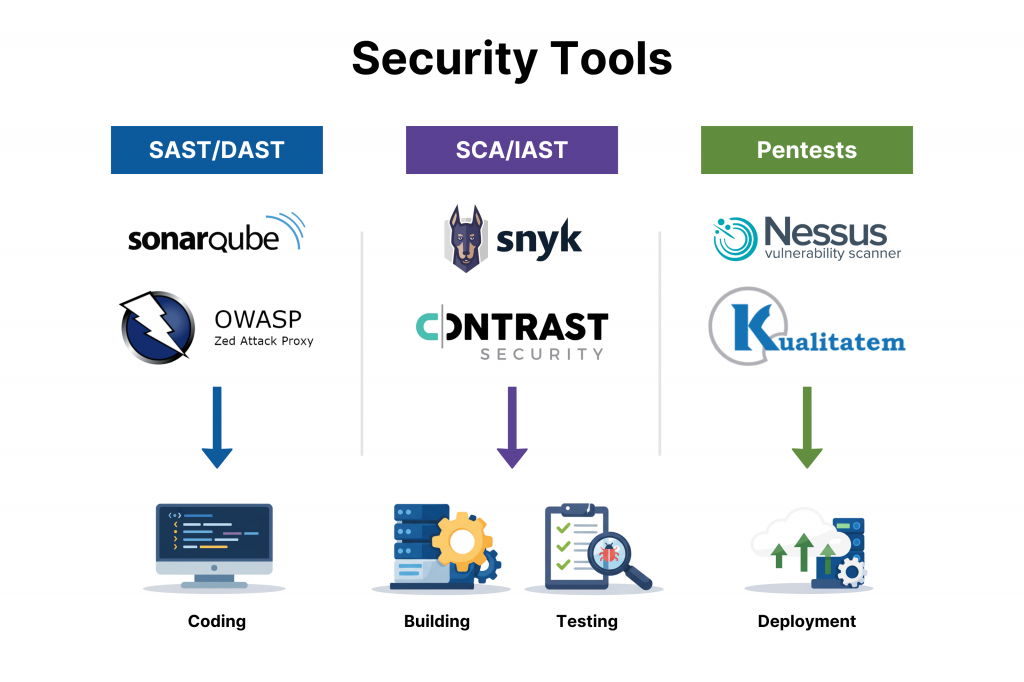
| Category | Tools/Services | Pipeline Fit | Key Use Case |
| SAST/DAST | Checkmarx, SonarQube, OWASP ZAP | GitHub Actions/Jenkins PR gates | Code scans & runtime probes |
| SCA/IAST | Snyk, Contrast Security | Build/Deploy stages | Dependency CVEs & interactive analysis |
| Pentest/Network | Burp Suite, Nessus, Nmap, Wireshark, Metasploit | Pre-release scans | Exploit simulation & traffic inspection |
| Full-Stack Services | Kualitatem Security Services | Enterprise CI/CD | Unified QA-security tracking & audits |
Metrics, Reporting, and Continuous Improvement
Effective security testing best practices rely on measurable KPIs to demonstrate ROI and drive ongoing enhancements in a secure SDLC.
Key Performance Indicators (KPIs)
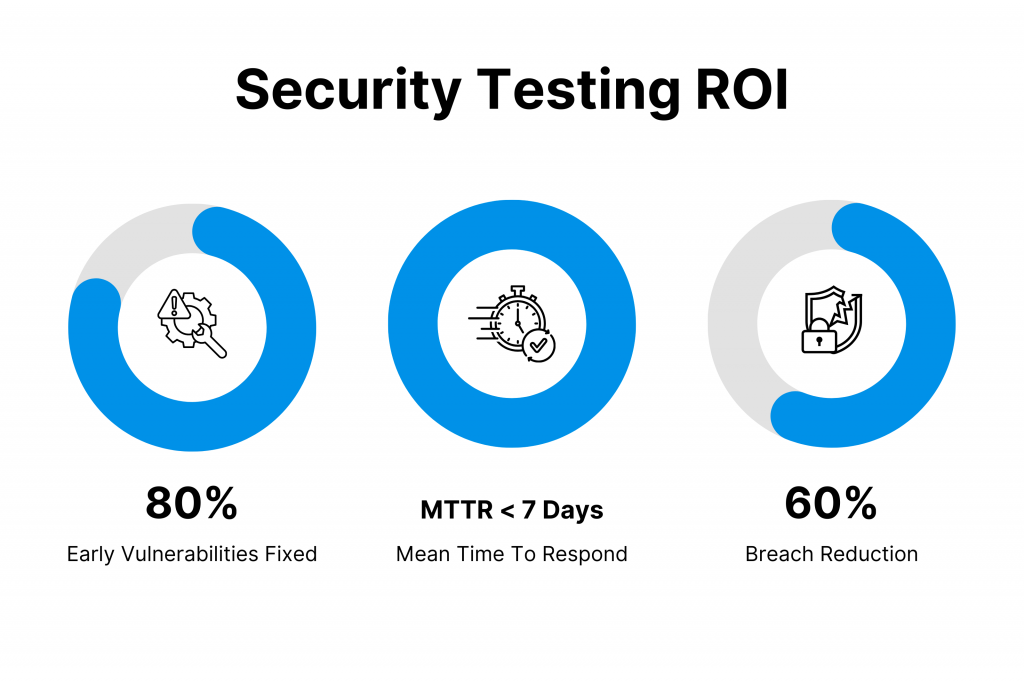
Track core metrics, such as:
- Vulnerabilities fixed early (target 80% pre-production)
- Mean time to remediate (MTTR under 7 days)
- Year-over-year breach reduction
These quantify how security shift-left in SDLC minimizes risks and costs, providing data-backed justification for investments in DevSecOps security testing.
Visualization and Reporting
Dashboards from tools like SonarQube, Snyk or Splunk display CVSS scores, compliance rates, scan pass/fail trends and remediation velocity.
Custom integrations with Grafana or ELK Stack offer real-time views, helping QA leads spot bottlenecks and prioritize high-impact fixes across teams.
Addressing Developer Pain Points
We’ve seen a few common struggles: metrics prove automation’s value by showing faster delivery (up to 30% velocity gains) without accruing security debt, silencing debates over tool overhead.
They also justify budgets, linking security spend to avoided breaches and regulatory wins.
Strategies for Continuous Improvement
The following are some strategies to keep in mind for continuous improvement of security testing in SDLC.
- Conduct quarterly reviews of KPI trends
- A/B test pipeline gates
- Automate remediation playbooks for low-risk issues
Foster a feedback loop with post-mortems on escaped vulnerabilities, ensuring application security testing in SDLC evolves with threats. Mature programs usually see 50% fewer incidents over time.
Integrate these into Agile retrospectives for cultural buy-in, turning metrics from compliance checkboxes into drivers of innovation and trust.
Conclusion
To wrap up, security testing is an essential part of the SDLC that helps identify risks early and prevent costly breaches later.
By integrating security checks throughout the development process, you ensure a safer, faster, and more reliable product. With the right combination of automated and manual testing, along with continuous monitoring, teams can stay ahead of emerging threats.
Lastly, keep in mind that adopting a security-first mindset is key to building trust and staying compliant. So, prioritize security, integrate it, and you’ll protect both your software and your reputation.
Discover Kualitatem’s expert testing services, including automation, performance, and accessibility testing. Ensure your software performs flawlessly at every stage.
Frequently Asked Questions (FAQs)
Q) What is secure SDLC?
It’s basically the software development lifecycle integrating security via shift-left, DevSecOps, NIST SSDF/OWASP for proactive protection.
Q) What are the main types of security testing?
SAST, DAST, IAST, SCA, and manual pentests.
Q) When should security testing be done in the SDLC?
Continuously across all phases, especially CI/CD.
What’s the difference between static and dynamic security testing?
Static (SAST) scans code without execution. While dynamic (DAST) tests live apps.
Why shift security left in SDLC?
Because it detects flaws early, reduces costs 100x, and maintains Agile speed.