Why Penetration Testing Services Are Critical for Modern Businesses

- December 31, 2025
- Zunnoor Zafar
Penetration testing services simulate real-world cyberattacks to expose vulnerabilities before hackers exploit them.
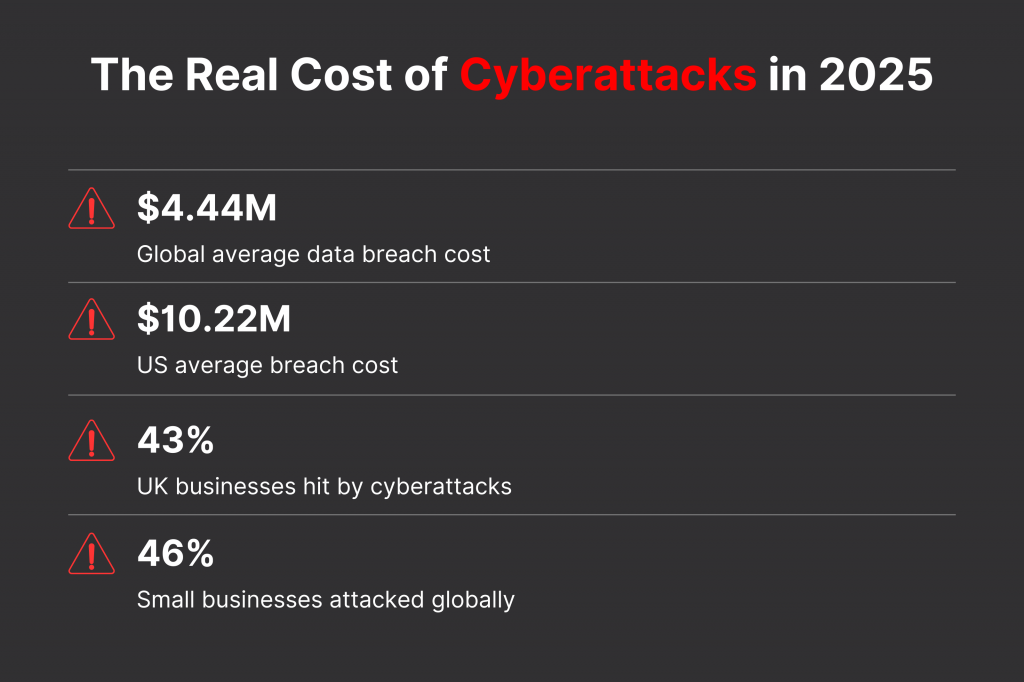
They play a huge role in safeguarding modern businesses from escalating threats. In 2025, average data breach costs hit $4.44 million globally, and U.S. breaches averaged $10.22 million.
To tackle this, penetration testing services deliver actionable insights beyond just basic scans. For fintech organizations, sometimes, functional testing is paired with pen tests to ensure both quality and security in software development.
That said, let’s discuss in detail why pen testing is so important for businesses today.
Key Takeaways
- Cyber-attacks are very common now. In 2025, a single data breach cost businesses about $4.44 million worldwide and $10.22 million in the US. In the UK, 43% of companies were hit by cyber-attacks.
- Penetration testing is more than just running tools. Real testers act like hackers and find serious problems that automated scans miss, such as logic flaws and chained attacks.
- Small and medium businesses are not safe either. About 46% were attacked, losing around $120,000 per breach, and 60% of them shut down within six months after a major incident.
- Scanning and penetration testing are different. Scans are quick and cheap, but penetration testing shows how attackers can actually break in and cause damage. This helps companies fix the most dangerous issues first.
- Regular testing is critical. Many companies test every three months or after major changes, which helps reduce fix costs by 30 to 50%. It also helps avoid expensive breaches later.
What is Penetration Testing?
Penetration testing is also often called ethical hacking. It deploys certified experts to mimic malicious actors probing networks, web applications, APIs, mobile apps and cloud systems for exploitable weaknesses.
Unlike automated QA processes that verify functionality and performance, pen testing uncovers subtle security flaws. These flaws can be business logic errors, privilege escalations or chained vulnerabilities that tools alone miss.
This hands-on methodology follows standards like OWASP, NIST SP 800-115 or PTES, providing businesses with prioritized remediation steps. Those that are integrated into the software testing lifecycle (STLC).
Kualitatem leverages this expertise to offer penetration testing alongside other QA services. So, contact us today and get a free quote along with a testing strategy.
Why Modern Businesses Are More Exposed Than Ever
Cyber threats have reached unprecedented levels in 2025, intensifying the vulnerability of businesses worldwide.
Get this, in the UK alone, 43% of businesses reported breaches or cyberattacks. Even though it’s a slight dip from 50% in 2024 yet still disproportionately affecting medium-sized firms (67%) and large enterprises (74%). Phishing remains the top initial attack vector at 31% of incidents.
Furthermore, globally, small and medium-sized businesses (SMBs) bear the brunt, facing a 46% cyberattack rate where incidents occur every 11 seconds on average. This leads to $120,000 in losses per breach and forcing 60% of victims to shutter within six months.
Ransomware has also surged alarmingly, impacting 1% of UK businesses (roughly 19,000 firms) and 59% of organizations overall.
Key amplifying factors driving this exposure include:
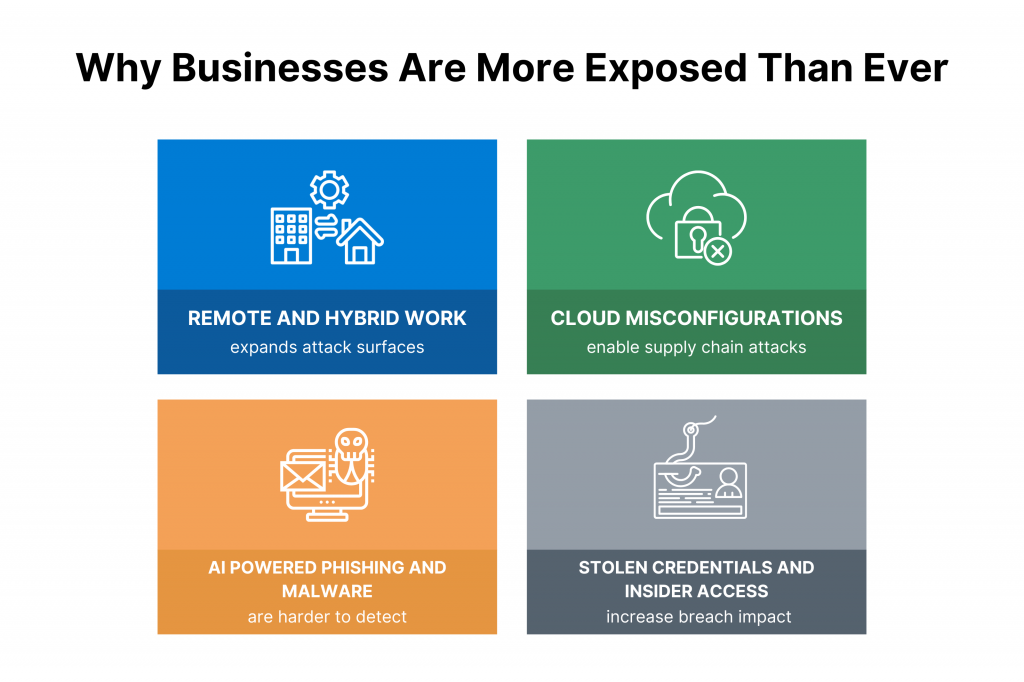
- Remote and Hybrid Work Models: With 61% of SMBs targeted, distributed teams expand attack surfaces via unsecured home networks and VPNs. This contributes to 75% of small businesses enduring at least one attack annually.
- Cloud Migration and Third-Party Dependencies: Rapid adoption leaves misconfigurations ripe for exploitation. What this does is fuel supply chain attacks.
- AI-Enhanced Threats: Attackers leverage generative AI for sophisticated phishing (3.4 billion spam emails daily) and malware (18% of attacks), outpacing defenses where only 14% of SMBs feel adequately prepared.
- Credential Theft and Insider Risks: Stolen credentials contribute to small business breaches, with average costs escalating amid a lack of multi-factor authentication in many setups.
What Penetration Testing Actually Covers
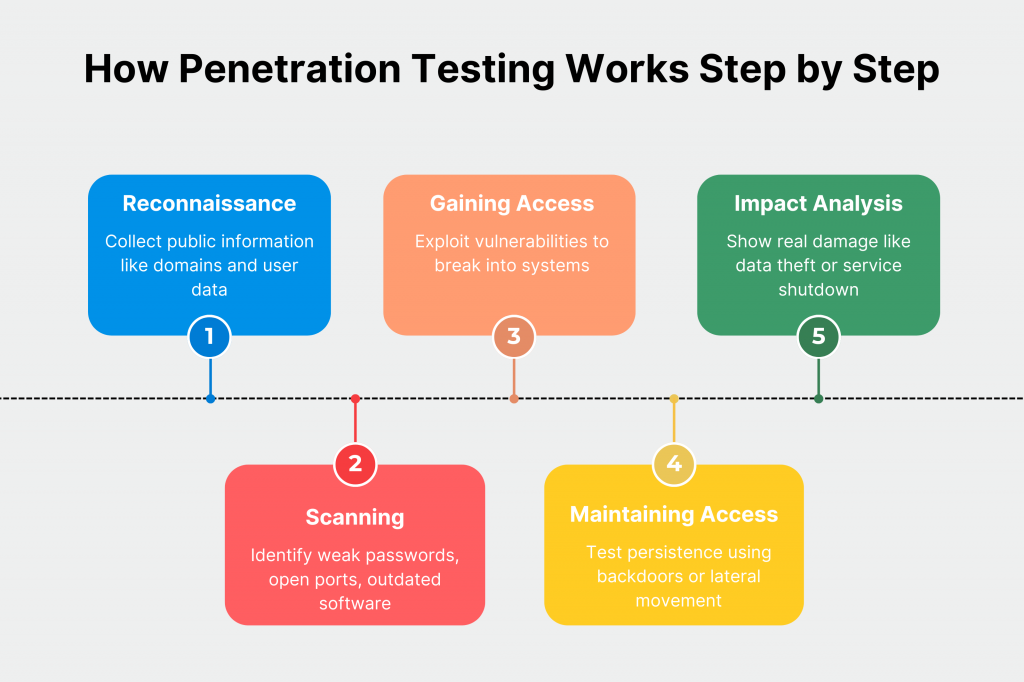
As mentioned earlier, penetration testing follows a clear step-by-step process to act like real hackers and find weak spots in your systems before the bad guys do.
Pen test experts start with simple info gathering. Then they check for problems and try to break in. After that, they stay inside the system to explore and finally show what damage could happen, like stealing data.
This hands-on work goes beyond quick automated checks to spot tricky issues that could lead to big problems.
Here’s what the main phases look like in plain terms:
- Reconnaissance: Experts collect public info about your setup, like employee names or server details. They do it to plan their attack, just like hackers do for free.
- Scanning: They use tools to scan for open doors, like weak passwords or outdated software, but also look deeper manually.
- Gaining Access: Then they try real exploits, such as injecting fake code, to actually break in and prove it’s possible.
- Maintaining Persistence: Once inside, they test if they can hide and move around, like installing backdoors.
- Analyzing Impacts: They show the real harm, such as grabbing customer data or shutting down services, with proof.
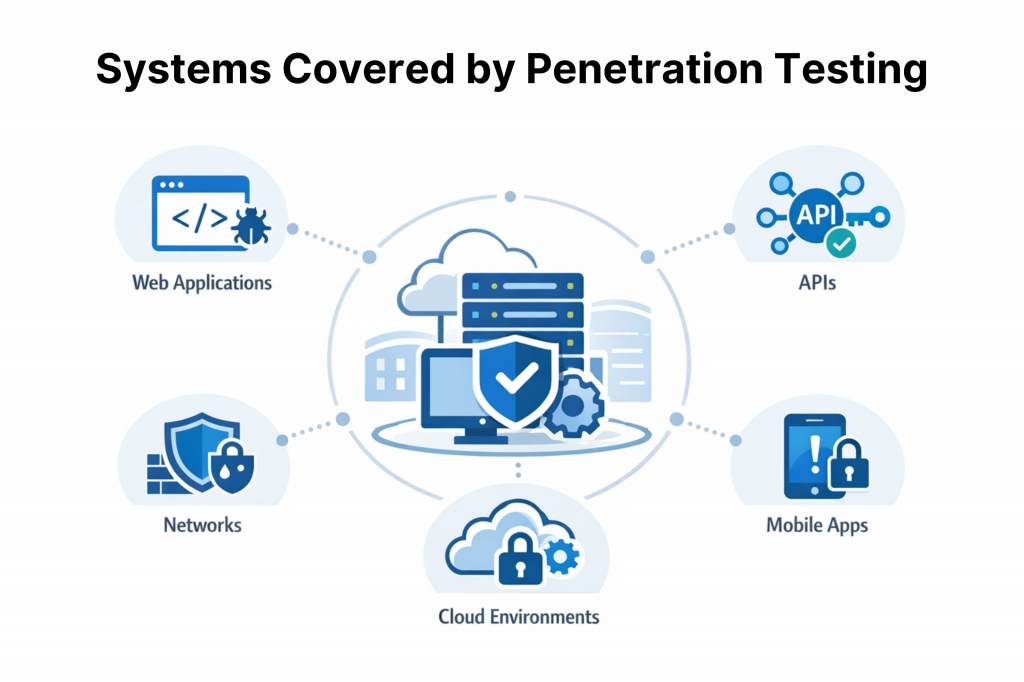
Besides this, penetration testing checks key areas where attacks hit hardest, which can be:
- Web apps: Things like SQL injection (tricking databases) or XSS (running bad scripts in browsers).
- APIs: Weak spots in how apps talk, like skipping login checks.
- Networks: Misconfigured firewalls or routers that let intruders roam.
- Mobile apps: Unsafe data storage on phones that leaks info.
- Cloud setups: Bad user permissions (IAM) that give too much access.
Unlike QA testing, which makes sure apps work right and feel good to users, pen testing thinks like a criminal. It chains small flaws together. For example, starting with a fake email (phishing), then jumping to your main servers (lateral movement), to show true dangers that auto-scans miss.
Fortunately, Kualitatem fits this right into your software testing lifecycle (STLC), with live checks during development.
Vulnerability Scanning vs. Penetration Testing
We’ve seen QA peeps who confuse vulnerability scanning and penetration testing. While both help find security weak spots, they work in different ways.
Scanning is like a quick robot check that lists possible problems fast. Whereas penetration testing is like hiring a pro hacker to actually try breaking in and show the real danger. Scans are okay for basics, but miss big issues like tricky logic flaws that let attackers sneak through.
Additionally, scanning uses automated tools like Nessus or Qualys to check for known bugs, such as old software versions or easy passwords. It spits out a long list of risks, but doesn’t prove if hackers can really use them. Lots of false alarms happen.
This makes it great for daily or weekly checks on big systems without much effort.
Penetration testing goes deeper with human experts. They link small flaws together into full attack stories, like using a weak login to steal data or take over servers. This proves the business harm, such as losing customer info or downtime, and gives clear fix steps.
It’s slower and costs more, but catches what machines can’t, like custom app tricks.
| Aspect | Vulnerability Scanning | Penetration Testing |
| Method | Automated tools check for known issues | Manual + automated, simulates full attacks |
| Output | List of potential flaws, no proof | Exploit proofs, attack paths, business impact |
| Depth | Surface-level, misses logic flaws | Chains vulnerabilities, real-world risks |
| Frequency | Weekly/daily for monitoring | Quarterly/annual or after changes |
| Cost & Time | Low cost, fast | Higher cost, 1-4 weeks |
| Best For | Quick checks, compliance scans | Remediation, audits, high-risk apps |
Business Benefits of Penetration Testing Services
Penetration testing services help businesses spot and fix security holes before hackers do, cutting down big risks in simple ways.
The global market for these services hit $1,862.4 million in 2025, growing fast at 18.20% yearly through 2033 because threats keep rising. It saves money by focusing fixes on the worst problems first, dodging average breach costs of $4.44 million, and helps teams respond more quickly to attacks. Insider threats alone cost $4.92 million each time.
For online shops or software companies, it stops attacks like DDoS that hit 20% of small businesses or ransomware that struck 59% of groups last year. This keeps sites running and money flowing.
Over time, it pays off big by building smarter security habits, especially since only 49% of hit companies even plan to boost defenses afterward.
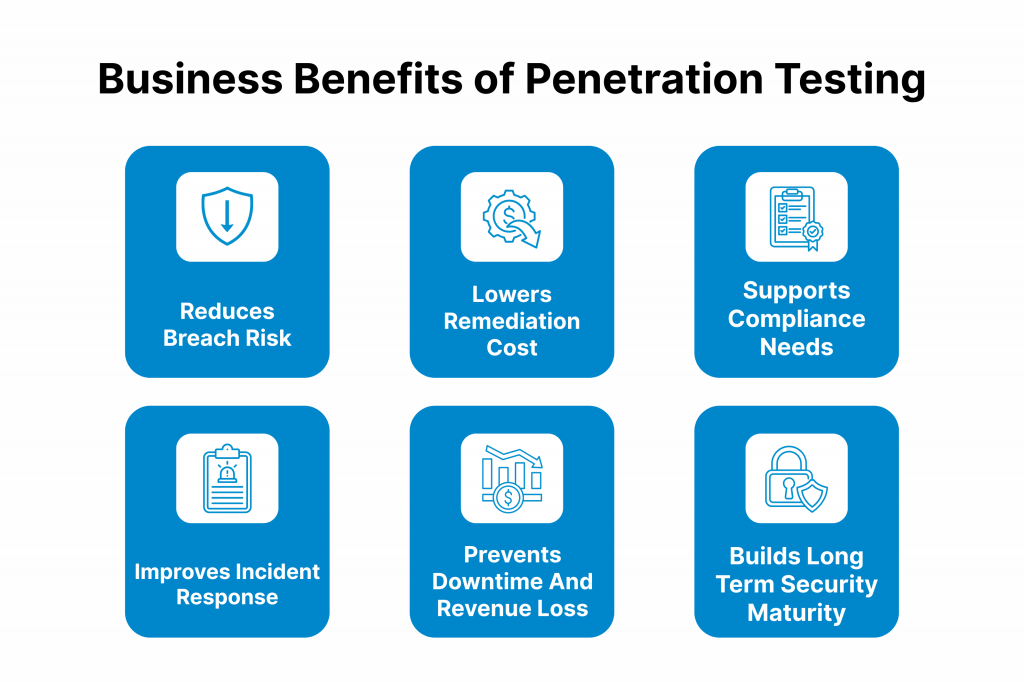
Here are the key benefits:
- Lowers Breach Risks: Finds hidden flaws that automated tools miss, like weak links in apps, preventing data theft or shutdowns.
- Saves Remediation Money: Prioritizes fixes to cut costs by 30-50%, acting early before small issues grow huge.
- Meets Compliance Needs: Proves you’re serious about rules like PCI DSS, avoiding fines and keeping customers happy.
- Boosts Response Speed: Trains teams on real attack paths, sharpening plans against phishing or malware hits.
- Protects Revenue: Stops downtime from common attacks. Ransomware alone locks out 1% of UK firms yearly.
- Builds Long-Term ROI: Creates a security mindset that pays back through fewer incidents and stronger trust.
Kualitatem makes this practical by tying penetration testing to QA, delivering real fixes that keep your business safe.
How Often Should You Run Penetration Tests?
Deciding how often to run penetration tests depends on your business risks, the rules you must follow, and recent changes.
A good rule from PCI DSS says to do external tests every three months and internal ones once a year. Furthermore, it is recommended that you always test after big updates, like new code releases or server changes, just so you can catch new weak spots right away.
It goes without saying that high-risk areas like banks or hospitals need tests more often. So, go ahead with weekly automated scans for steady checks and make monthly regular tests a must.
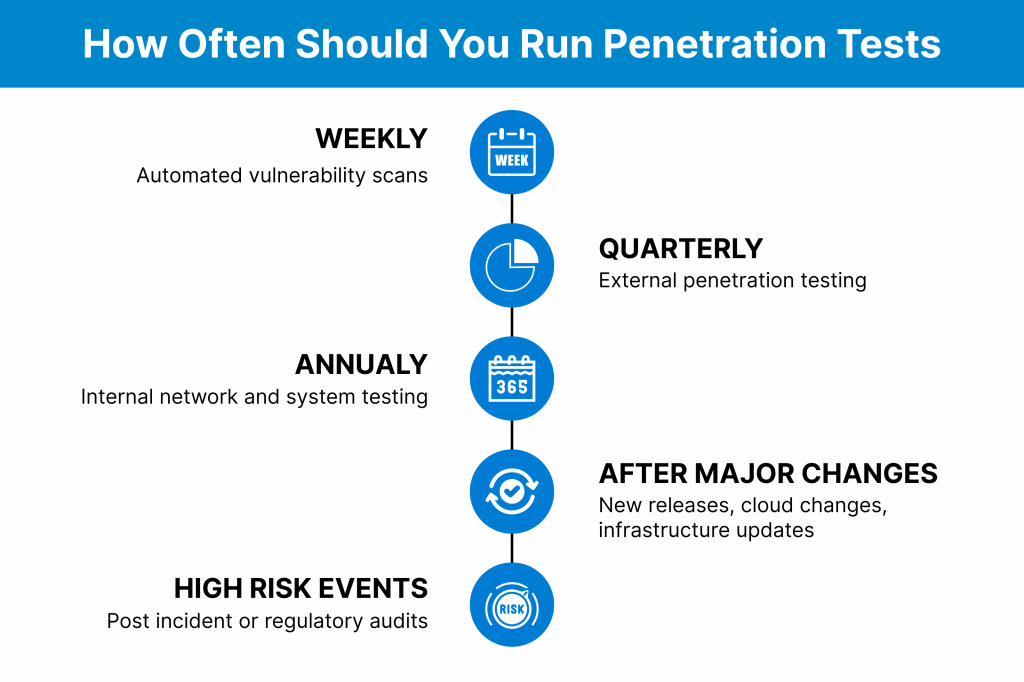
Here’s a simple guide to pick the right schedule:
- Quarterly (Every 3 Months): External tests for internet-facing stuff, like websites or APIs. This is required for PCI DSS to stay compliant.
- Annually (Once a Year): Full internal tests on networks and internal apps, or more if you’re in finance/healthcare.
- After Changes: Right after code deploys, new cloud setups, or big patches. Don’t wait for the next cycle.
- High-Risk Times: Extra tests post-ransomware scares or if audits/clients demand it.
- Ongoing Pairing: Weekly vulnerability scans + quarterly pen tests for full coverage without overload.
- For Small Businesses: Start quarterly if budget-tight, but prioritize if you lack endpoint tools.
What a High Quality Pen Test Deliverable Should Include
A good penetration test report isn’t just a list of problems. It’s a clear guide that shows what could go wrong, why it matters to your business and exactly how to fix it.
Bad reports feel like checkboxes with no real help, which frustrates teams who want actionable advice, not vague warnings.
Top reports start with simple executive summaries that tie risks to real money losses.
Hence, look for these key parts in a quality deliverable:
- Executive Summary: Short overview for bosses, explaining top risks in business terms like “This flaw could leak customer data and cost $500K in fines,” with charts for quick reads.
- Vulnerability Details: Each issue is scored by CVSS (e.g., 9.8 critical), with proof-of-concept (PoC) exploits showing how an attacker breaks in step-by-step.
- Attack Paths: Maps of how small flaws chain together, like weak login + bad permissions leading to full server takeover, proving real danger.
- Affected Assets: Lists exactly which servers, apps, or users are hit, so devs know where to focus.
- Remediation Roadmaps: Step-by-step fixes with timelines (e.g., “Patch in 7 days”), code snippets, and who does what. All prioritized by risk.
- Business Impact: Dollar estimates, downtime risks, or compliance fails, like PCI DSS violations.
- Retest Results: Proof fixes worked, with follow-up scans or re-exploits to confirm.
Kualitatem stands out by delivering these full packages. You get real-time audits during your QA process, along with retests until issues are gone. Check out our case studies.
Common Mistakes Businesses Make When Choosing a Pen Testing Service Provider
Buying penetration testing services sounds simple, but many businesses pick the wrong provider and end up with weak protection or wasted money.
They chase cheap options or skip key checks, leading to reports that don’t help. This leaves gaps that hackers exploit.
Below is a breakdown of the top mistakes to avoid.
1. Choosing Cheap Automated Scans Over Manual Testing
Many go for low-cost scans that focus on basic malware checks, thinking it’s enough. These scans miss chained exploits where small flaws combine into big breaches.
Real manual testing by experts finds hidden issues scans ignore. Skipping it saves pennies now and costs millions later in breach recovery.
2. Skipping Retesting After Fixes
Some businesses have security policies, but they forget to retest after patches.
Remember, hackers won’t wait. You need proof that the fixes worked. Without retests, the same doors stay open, turning one-time tests into ongoing risks.
3. Ignoring Proper Scoping, Like Business Logic Tests
Teams often define tests too narrowly, skipping business logic flaws (e.g., bypassing checkout rules).
This leaves apps vulnerable to clever attacks. Always scope for your full setup, i.e., web, API, mobile, to cover real threats, not just surface checks.
4. Overlooking Tester Certifications
Buyers skip checking for certs like OSCP or CEH, hiring juniors who miss complex issues.
Certified pros follow proven methods and spot what newbies can’t. We’ve seen people on Reddit communities rant about shallow reports from uncertified teams. To make sure this doesn’t happen to you, demand proof of expertise upfront.
5. Mismatching Methodology to Your Needs
Not aligning tests to standards like OWASP or PCI DSS creates compliance holes, such as missing internal scans required quarterly.
Generic approaches fail audits. So, match the provider’s methods to your industry and rules for real value.
Final Words
Penetration testing services are a must-have for any modern business fighting off cyber threats.
With attacks hitting 43% of UK firms and breaches costing millions, skipping these tests leaves you wide open to hackers, downtime and lost trust. They go beyond basic scans to uncover real weaknesses, cut risks, meet compliance rules like PCI DSS, and save big on fixes before problems explode.
Additionally, don’t settle for checkbox reports that gather dust. Pick a partner that delivers clear, actionable advice with proofs-of-concept, step-by-step fixes and retests to make sure everything works.
Kualitatem offers all this, which makes it a smart choice for teams wanting senior-level expertise tied to QA services.
Frequently Asked Questions (FAQs)
Q1) What types of businesses need penetration testing services the most?
High-risk ones like finance, healthcare, e-commerce, and SaaS. Basically, anyone handling sensitive data should prioritize it for protection.
Q2) What are the different types of penetration testing services available?
Web app/API, network, mobile app, and cloud testing. Kualitatem covers all of these, integrated with QA.
Each targets specific assets like SQL injection or IAM flaws.
Q3) Is penetration testing required for SaaS companies selling to enterprises?
Often, yes. Via client demands, SOC 2 or ISO 27001 to avoid breaches. It proves security in vendor reviews.
Q4) What happens after a penetration test is completed?
Receive report with fixes, remediate, retest for verification and schedule next. If done right, you get lasting security.