Keeping Your Business Secure With Penetration Testing Services
- February 21, 2023
- admin
Everyone knows that in order to keep your business safe, you need to have strong security measures in place. Even the most sophisticated cyberattacks do not pose a complete security threat until they are introduced into your organization’s systems. In order to ensure that your company’s information remains confidential, secure and safe from hackers and other cybercriminals, you need to implement proper security measures. If left unattended, confidential data can be stolen and used for malicious purposes. To keep your business safe from hackers and other cybercriminals, you need to hire security auditors who specialize in testing for weaknesses in your websites, applications and computer networks. While penetration testing services may seem like an intimidating process, they actually offer plenty of benefits for businesses looking to remain secure against cybercriminals.
In this article we will briefly discuss penetration testing, its types, benefits and a few tips on how you can prepare for pen testing.
What is Penetration Testing?
A cyber-security professional will try to identify and exploit weaknesses in a computer system during a security exercise known as penetration testing also known as Pen Testing. The goal of this simulated assault is to locate any security gaps that an attacker may exploit.
It’s like a bank hiring a thief to break into their building and vault. If the thief succeeds, the bank can use the experience to improve their security.
Types of Pen Testing
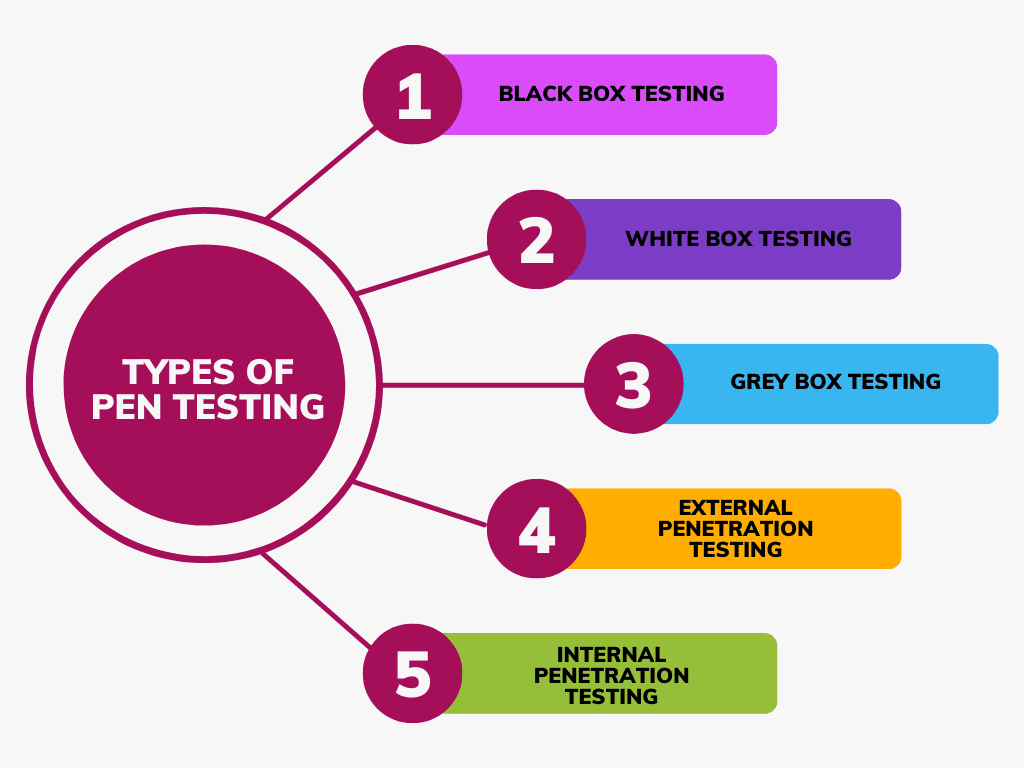
Black Box Testing
This type of testing involves simulating an attack on a system without any prior knowledge of the system’s internal workings. The testers are given no information about the system’s architecture, code, or network topology. This testing mimics an attacker’s approach to a system, providing a valuable method for evaluating a system’s external security posture.
White Box Testing
For this kind of testing, the system’s source code and network topology are all fully accessible to the testers. This type of testing is used to evaluate the internal security of a system and is often used by organizations to comply with regulatory requirements.
Grey Box Testing
We combine black box and white box testing to create gray box testing. The testers are provided with some knowledge about the system’s architecture, code, or network topology, but not the full picture. The purpose of this kind of testing is to simulate attacks when the attacker is familiar with the system.
External Penetration Testing
This kind of testing simulates an intrusion coming from the outside, like the internet. The goal is to identify vulnerabilities in a system’s perimeter defenses, such as firewalls and intrusion detection systems.
Internal Penetration Testing
Internal penetration testing is focused on identifying vulnerabilities in a system from within the organization’s network. The goal is to simulate an attack by a malicious insider or an attacker who has gained access to the network.
Benefits of Penetration Testing
Identify Vulnerabilities
Before an attacker can take advantage of a system’s weaknesses and vulnerabilities, penetration testing can assist uncover them. By simulating a real-world attack, testers can discover and document vulnerabilities that may have gone unnoticed otherwise. This information can increase the overall security of the system and fix vulnerabilities.
Compliance
Many industries have regulations that require regular security testing, including penetration testing. Organizations can comply with these rules and avoid penalties for non-compliance by using penetration testing.
Avoid Data Breaches
By identifying and remediating vulnerabilities, penetration testing can help organizations avoid data breaches that can result in the loss of sensitive data, reputational damage, and financial losses.
Cost-Effective
A practical technique to assess a system’s security is through penetration testing. The cost of a penetration test is minimal in comparison to the expense of a data breach. Organizations can lower the potential costs of a data breach by using penetration testing to find vulnerabilities before they can be exploited.
Improve Security Awareness
Penetration testing can help raise awareness of the importance of security among employees and management. By simulating a real-world attack, testers can demonstrate the impact of a successful attack and the importance of following security policies and best practices.
Continuous Improvement
Penetration testing can help organizations continuously improve their security posture by identifying vulnerabilities and weaknesses that need to be remediated. Organizations may stay ahead of developing threats and new attack methods by conducting regular penetration tests.
Tips to Help Implement Penetration Testing in Your Firm
Determine Your Risk and Threat Level
The first step in any security audit is to determine the risk level within your organization. This is important because it will help you identify any vulnerabilities that could pose a threat to your data or networks. If the risk level is very high, you may want to consider hiring auditing services from a company with a much lower risk level. But, even if you are at a moderate level of risk, you can still benefit from hiring a security audit.
Plan and Prepare
One of the most effective ways to prepare for a security audit is to plan ahead. One of the best things you can do is to create a cleanup plan. A cleanup plan is a set of actions you will take if a security incident occurs. If someone discovers a breach in your security, you must take steps to remove all traces of it.
Hire the Right People
When it comes to hiring a security audit firm, the best way to go is to do your research and hire the company with the highest rating from previous customers. When you hire a security audit firm, you will want to make sure that you get someone with experience in the field.
Test You, Your System and Your People
One of the best parts about hiring a security audit firm is that you get to choose which experts you want to work with. You can choose experts in security assessment or you can choose to choose for qualitative or quantitative metrics. For example, you can choose to actively hire based on qualitative metrics such as identifying a certain number of vulnerabilities or filing a specific number of reports against your company.
Conclusion
Pen testing services can be an effective way to find security issues in your infrastructure and applications. These services can test your websites, applications, and computer networks for a variety of issues such as poor user experience, data privacy risks, poor access control, and more. Additionally, they are very flexible, and you can use them for this purpose. When you find issues with your infrastructure or applications, you can hire a security audit company to help you fix them. As a result, You can ensure that your systems are secure and protect your users’ data. While hiring a security audit company is not an inexpensive process, it is definitely worth the investment.











