Vulnerability Assessment and Penetration Testing for E-business Platforms

- January 26, 2026
- Zunnoor Zafar
E-business platforms are everywhere. From online stores to service portals, you might’ve come across many by now. While these platforms contribute heavily to the economy, they are also highly susceptible to cyberattacks.
Protecting them requires very good security measures. But what measures are they? Well, there are quite a few. But two of them are vulnerability assessment and penetration testing (VAPT).
These two practices are considered essential for the safety of an e-business platform. This is because they help identify, evaluate, and eliminate security weaknesses before they are exploited by someone. We’ll talk more about VAPT in this article. So, let’s dive in.
Vulnerability Assessment and Penetration Testing Explained
VA and PT are two different things. However, they are often combined under the umbrella of VAPT.
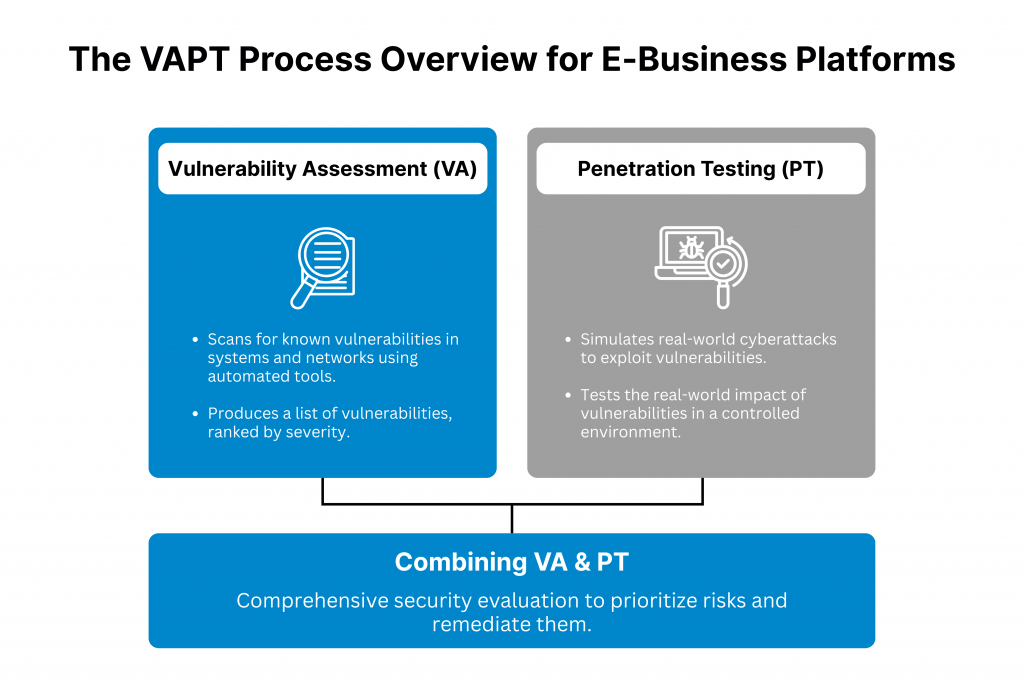
1. Vulnerability Assessment
To put it simply, this approach systematically checks applications, servers, and networks for weaknesses that are already known. The process is carried out by an SQA or by using automated tools.
Once the testing is completed, a list of potential vulnerabilities is produced. The weaknesses are ranked by risk.
2. Penetration Testing
Penetration testing goes a step further. It simulates real-world cyberattacks to exploit the known vulnerabilities. Everything is done in a controlled environment, and the intent of doing this isn’t malicious.
This is done to see how a hacker could compromise the platform and the extent of damage that they can do.
Combining both these approaches, a comprehensive security evaluation is carried out for e-business platforms, enabling organizations to prioritize and remediate risks.
Importance of VAPT for E-Business Platforms
E-business platforms handle a huge amount of customer data. This information is sensitive and can prove to be harmful if it falls into the wrong hands. For this reason alone, it is a prime target for cybercriminals. VAPT prevents this from happening. Some other reasons why it is so important are:
- Ensure Business Continuity: Data loss or outages are prevented with VAPT. This leads to seamless and continuous business operations.
- Meet Compliance and Avoid Fines: Many standards, like PCI DSS for payments or GDPR for data privacy, require regular security testing. Failing to do so can result in fines. VAPD helps avoid this by helping businesses stay in line.
- Maintain Customer Trust: Businesses that do regular VAPD are basically demonstrating to their customers that security is taken seriously. A breach-free record and transparent security measures can build confidence in clients.
- Reduce Financial and Legal Risk: It is a no-brainer that a successful attack can lead to expensive recovery costs. It can also result in legal action and lost sales. Preventing issues through VAPT will always be cheaper than dealing with the fallout of a breach.
VAPT Methodology for E-Business Platforms
The VAPT process for e-business platforms usually consists of these phases:
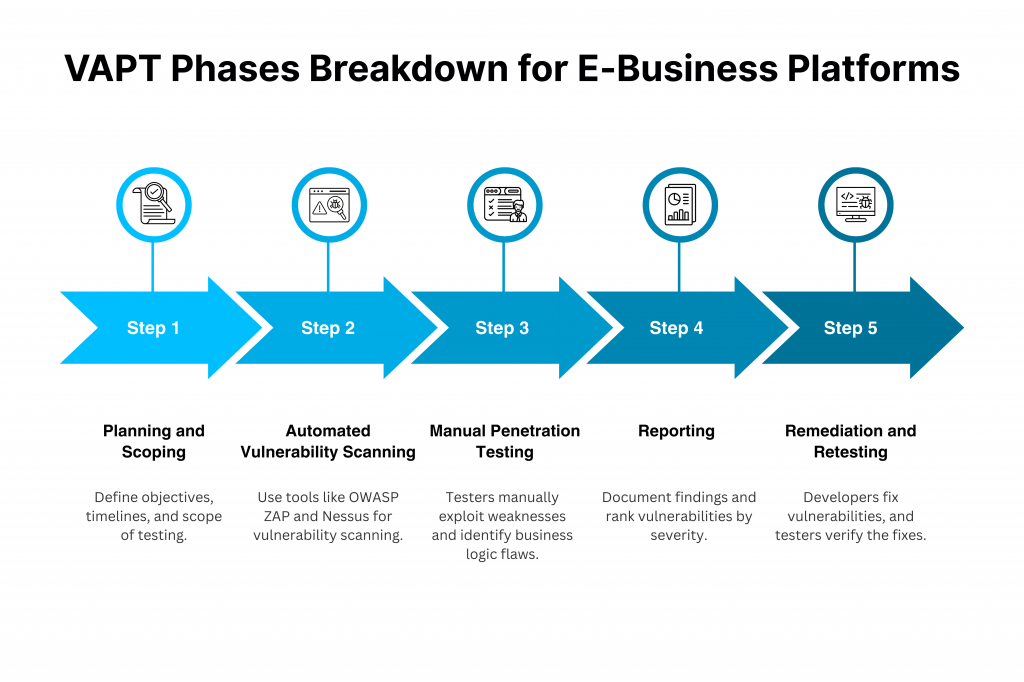
1. Planning and Scoping
To start things off, the parts of an application that are supposed to be tested are defined. Timelines are established and testing limitations, along with objectives aligned with business needs, are highlighted.
2. Automated Vulnerability Scanning
Automated tools, such as OWASP ZAP or Nessus, are used to scan the defined parts of an application. This highlights common vulnerabilities, and an initial list of them is created.
3. Manual Penetration Testing
The scan results and the initial list are then used as a guide. Testers attempt to analyze these weaknesses manually and even exploit them using techniques such as code injection to understand the risk they carry.
Not only that, but business logic flaws that automated tools may miss are also highlighted manually.
4. Reporting
This phase includes documenting each of the confirmed security weaknesses in detail. Where the weakness was found, how it was exploited, and what was the impact of its exploitation are all mentioned.
Issues are ranked by severity so the team knows which ones they’re supposed to fix first. The reports are usually tailored to different audiences, from executives to technical teams, so clarity can be ensured.
5. Remediation and Retesting
At last, developers fix the highlighted issues. They apply the patch and let the testers know, who then re-run scans or specific tests to verify the fixes.
This methodology, if applied before each major release, helps in making sure that the e-business’s security is impenetrable.
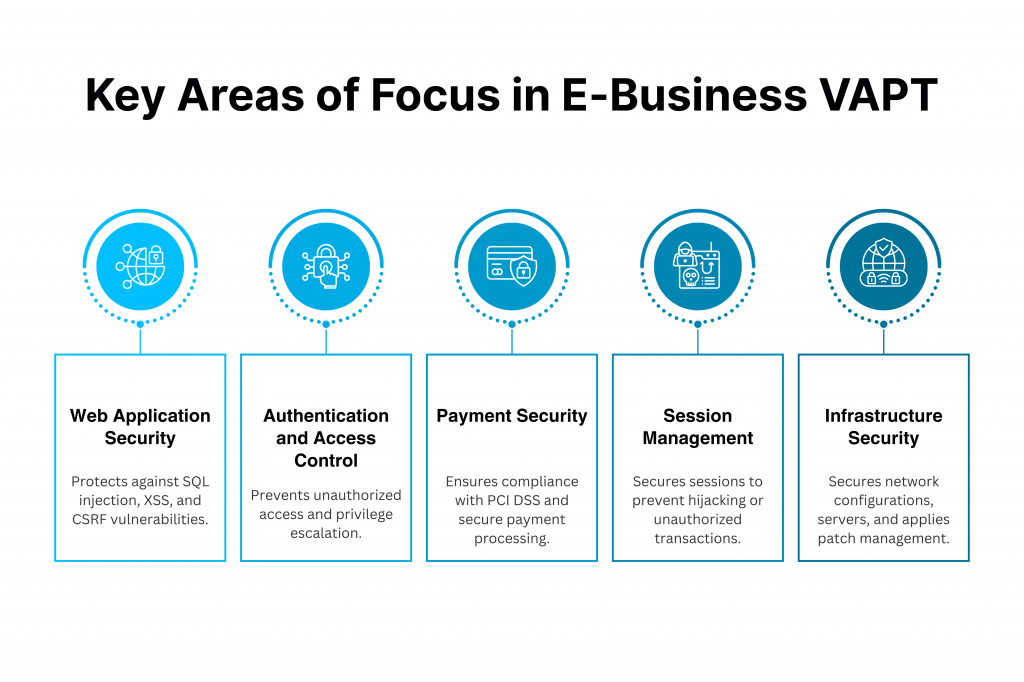
Key Areas of Focus in E-business VAPT
There are some areas in an e-business model that require the most of your attention. Do yourself a favour and double-check the following for security weaknesses.
- Web Application Security: Common vulnerabilities such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF) should always be first on your list. This protects both the online storefront and user interactions.
- Authentication and Access Control: Unauthorized access and privilege escalation have to be avoided at all costs. If this is not done right, security breaches are imminent.
- Payment Security: All payment gateways should be assessed multiple times, and data should be handled in accordance with the PCI DSS standards to prevent fraud.
- Session Management: Every session has to be secured and validated so there’s no chance of hijacking or unauthorized transactions.
- Infrastructure Security: Network configurations, server handling, and patch management should be done carefully to avoid any sort of slipups.
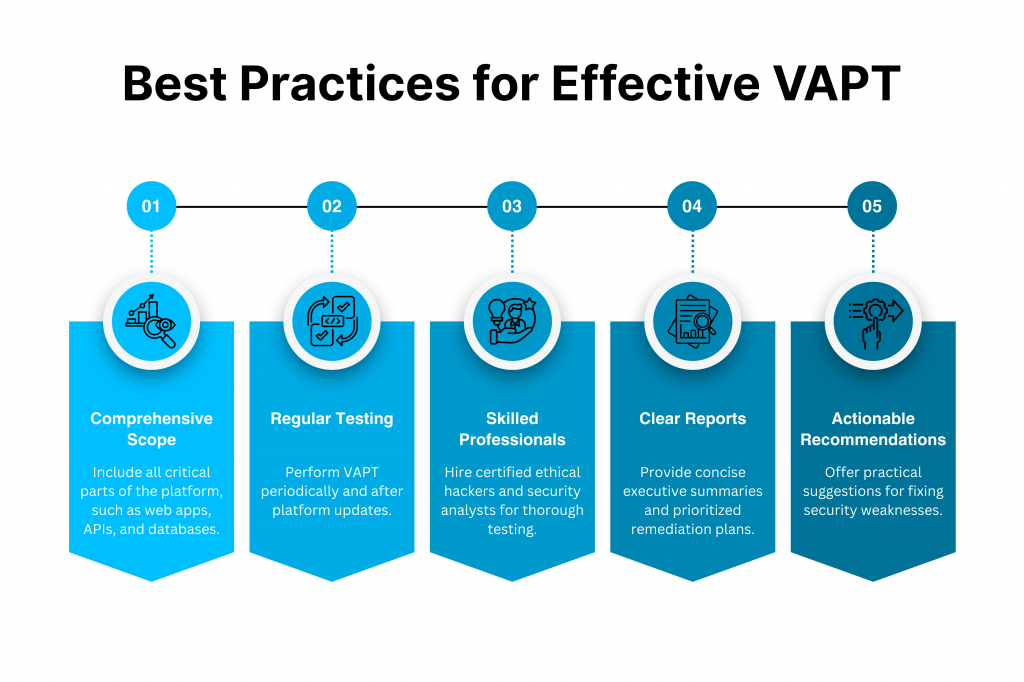
Best Practices for Effective VAPT in E-Business
To make the most out of VAPT for your online platform, consider the following practices.
- Comprehensive Scope: Be sure to include all the critical aspects in your testing. Web applications, APIs, databases, and payment systems are some of them.
- Regular Testing: We recommend conducting VAPT periodically, especially after you’ve rolled out a major update or made changes to the platform.
- Always Look Towards Skilled Professionals: Hire certified ethical hackers and security analysts to perform thorough testing.
- Create Clear Reports: The identified vulnerabilities should always be communicated clearly to the fixers and decision-makers. It’s best to provide concise executive summaries and prioritized remediation plans.
- Provide Actionable Recommendations: If you’re in charge of testing, always offer specific and practical suggestions to fix security weaknesses. These include patches, configuration changes, and policy updates.
Closing Thoughts
Usually, e-businesses are more susceptible to cyberattacks than other platforms. To ensure protection against one, vulnerability assessment and penetration testing (VAPT) are carried out.
The steps to do so involve thorough planning, automated scanning, human testing, reporting, and patching. Apart from this, the suggested practices for effective VAPT should be put into action for better results.
Kualitatem performs vulnerability assessment for you. Contact us today to safeguard your e-business platform from online threats.